Privilege Escalations
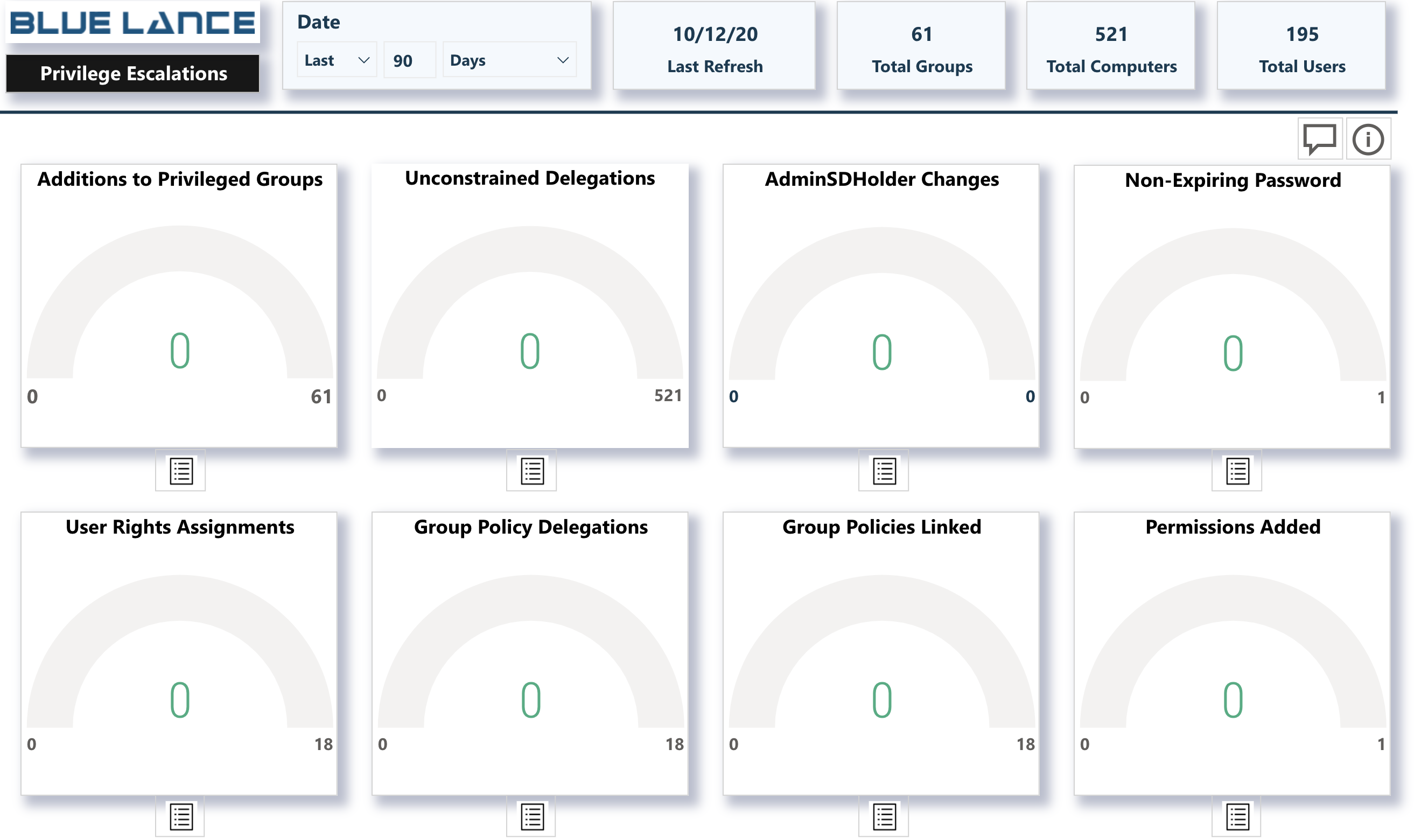
The Privilege Escalations sub-panel visual contains 8 metrics that indicate enhanced rights and access within the Active Directory infrastructure. The ideal scenario would be to see a 0 value on all metrics. In the event any metric displays a positive number, details of the escalation can be viewed by clicking the report icon just below the metric.
Visuals
- Addition to Privileged Groups – Users added to groups with enhanced privileges such as Administrators, Domain Admins or Enterprise Admins. Extreme caution must be taken when adding users to these groups as they have full rights to resources in the directory.
- Unconstrained Delegations – Unconstrained delegations give authority to a server allowing it to act on behalf of a client with other remote systems in an environment. This form of impersonation is a security risk because a compromised client can use an unconstrained server to get other servers or resources in the environment to perform tasks on the client’s behalf.
- AdminSDHolder changesThe Active Directory AdminSDHolder object manages the access control lists of members of built-in privileged Active Directory groups. All changes to permissions (ACLs), on this object, must be monitored to detect manipulation. Such changes could give attackers access to privileged accounts within the domain.
- Non-Expiring Password – Configuring a user account to have a password that never expires is a security risk for the organization. These accounts are not required to adhere to the organization’s password policies and could have very weak passwords.
- User Rights Assignment – User rights assignments are settings applied to the local devices on the network. They allow users to perform various system tasks, such as local logon, remote logon, backups, debug programs, impersonate a client etc. These rights can escalate privileges and need to be monitored.
- Group Policy Delegations – Group Policy Delegations delegate rights to other users which could mean escalation of rights. These delegations must be monitored to ensure that these assignments are not a mistake or malicious.
- Group Policies Linked – Linking a Group Policy to an OU activates rights to objects within the OU. This operation must be monitored to ensure that linking is not a mistake or malicious.
- Permissions Added – Provides a listing of all ACL changed that occurred for specified time frame.
