Account Lockouts
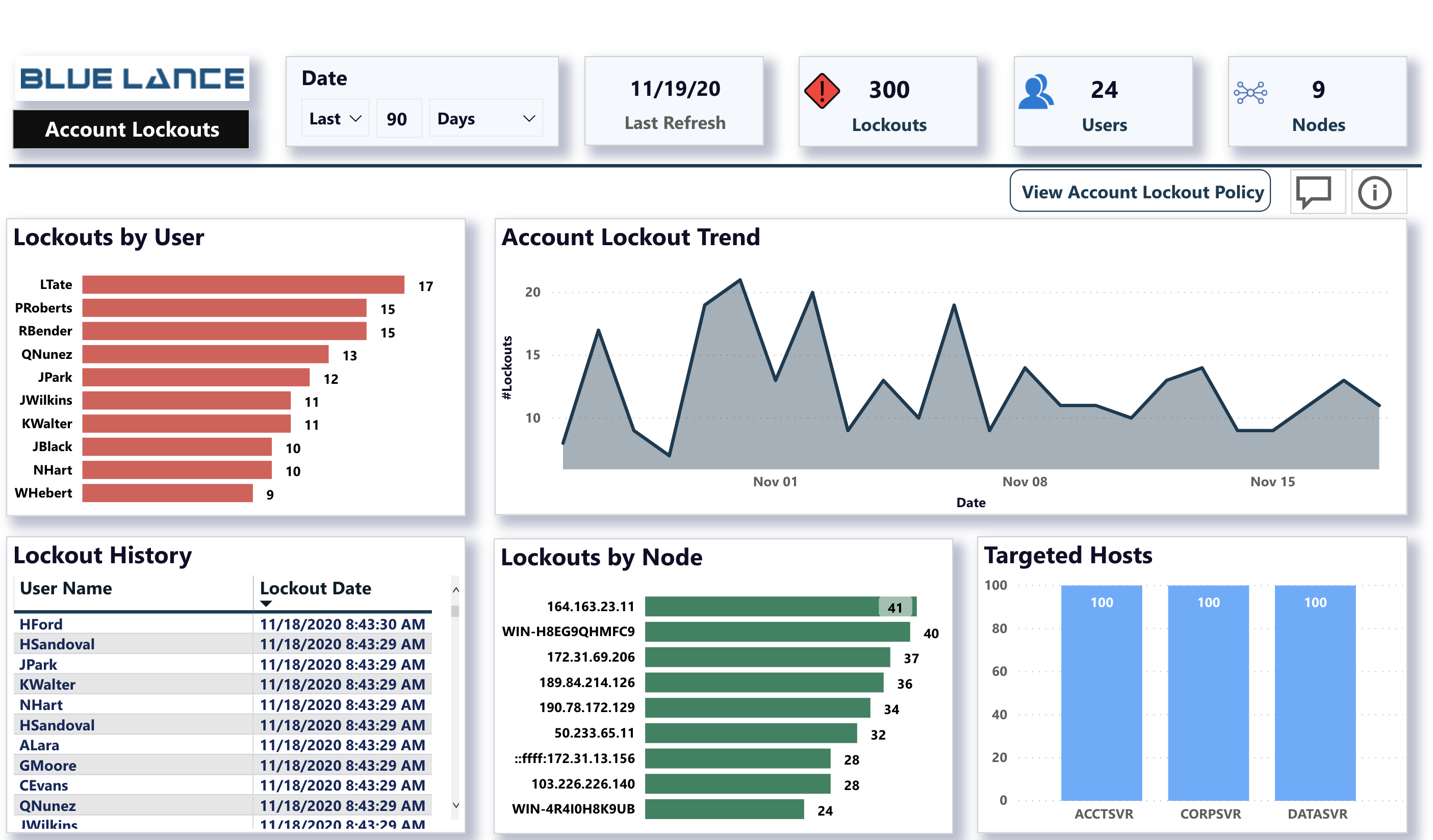
Account lockouts occur for a lot of reasons, as described below, but the challenge for Network Administrators is to pinpoint where lockouts happen. The Account Lockouts panel can help identify the source from where lockouts happen by pinpointing the source nodes of lockout incidents on targeted hosts.
Visuals
- Lockouts by User – List of user account lockouts for the time period selected. Click on a user to view the lockout history, nodes and hosts. Right-click and drill down to details for tabular reports
- Account Lockout Trend – Pattern of lockout activity that have occurred over selected time period. Click on any peak to identify users, nodes and hosts.
- Lockout History – Used to identify all timestamps of when lockouts for a user happened. Clicking on an entry will display the node address of where lockout occurred.
- Lockout by Node – Identify node address of where lockout occurs.
- Targeted Hosts – Hostnames where locked out users where attempting access.
- View Account Lockout Policy – Click to view the current domain lockout policy.
Account lockouts occur under the following scenarios:
1. Users forgetting their password
2. Passwords were changed but were not updated on certain devices
3. An attacker attempting to crack a password
The top 10 causes for account lockouts are:
1. Programs with cache credentials which do not change after a user changes their password
2. Cached service account passwords setup with the service control manager on member computers that use the account
3. Bad Password Threshold is set too low
4. Users who log on to multiple computers. Password changes on one computer are not used on other computers leading to a lockout.
5. Applications that store user names and password are not updated.
6. Scheduled processes that continue to use old credentials
7. Persistent drive mapping
8. Disconnected terminal server sessions
9. Active Directory replication issues
10. Service accounts configured to use user accounts
