Permissions Hygiene
Active Directory ACL’s (Access Control Lists) represent access control on all objects (Users, Groups, OU’s, Computers) within the directory. Discretionary access control (DACLS) defines trustees or principals granted access to an object. The LT Auditor+ Best Practices Permissions (ACLs) sub-panel are a set metrics that identifies DACLs that could potentially be exploited by an attacker.
Permission (ACLs) hygiene metrics look for the following DACL assignments:
• GenericAll – full rights to the object (add users to a group or reset user’s password)
• GenericWrite – update object’s attributes (Example: logon script)
• WriteOwner – change object owner to attacker-controlled user take over the object
• WriteDACL – modify object’s ACEs and give attacker full control right over the object
• AllExtendedRights – ability to add user to a group or reset password
• ForceChangePassword – ability to change user’s password
• Self (Self-Membership) – ability to add yourself to a group
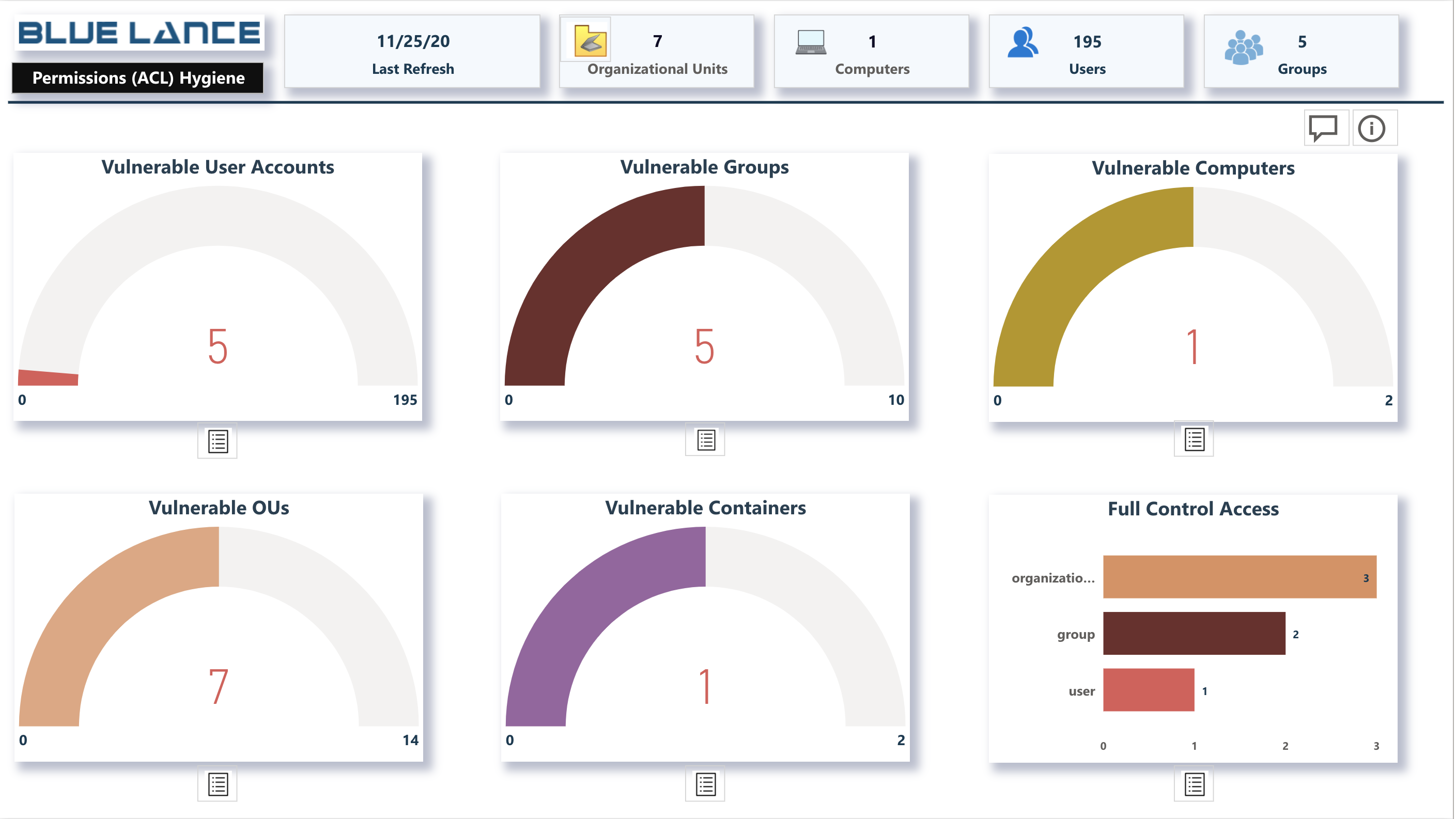
Visuals
- Vulnerable User Accounts – Principals or Trustees of these user accounts have the ability to reset the user account password and gain access.
- Vulnerable Groups – Principals or Trustees of these Groups have the ability to add members to the Group. This can be very dangerous if the Group has powerful privileges or has access to sensitive information.
- Vulnerable ComputersTrustees could gain code execution with elevated privileges on a computer they have WRITE privilege on that computer’s AD object. If a trustee account gets compromised the attacker could take over this computer to gain access.
- Vulnerable OUs – Lists all Principals with full rights to the OU (Organizational Unit) and all objects contained in it. Care should be taken to ensure access rights given are needed and that there are no violations of the principal of ‘Least Privileges’.
- Vulnerable Containers – Lists all Principals with full rights to Container and all objects contained in it. Care should be taken to ensure access rights given are needed and that there are no violations of the principal of ‘Least Privileges’.
- Full Control Access – Lists all objects with Principals that have full rights to Active Directory objects. The report can be used to ensure unnecessary rights have not been granted.
Coming soon
