Overview
On 12/13/2020, FireEye released a malware report on a new malware variant called “Sunburst Backdoor” that precipitated the Department of Homeland Security’s CISA (Cybersecurity and Infrastructure Agency) to issue an emergency directive.
The Sunburst malware ‘trojanized’ a legitimate application file called ‘SolarWinds.Orion.Core.BusinessLayer.dll’ from SolarWind’s Orion software which was subsequently distributed to their customers. Once infected, this ‘trojanized’ backdoor allows the adversary to move laterally on a victim’s network and exfiltrate critical data.
In response to the CISA Emergency Directive 21-01, BLUE LANCE is providing this high-level guidance to its customers on how to configure LT Auditor+ to detect SolarWinds SUNBURST malware and continuously protect their networks in real-time.
BLUE LANCE realizes this is a time of high pressure and uncertainty. We are providing this rapid response guidance to our customers with the goal of helping you to quickly assess, investigate, manage and proactively protect your networks from the SolarWinds SUNBURST malware in accordance with FireEye’s recommendations.
Our helpdesk and engineering teams are ready to assist you with this security incident. Please do not hesitate to contact us at 1-800-856-BLUE (2583) in the US, or +1-713-255-4800 from outside the US. You may also connect with us via chat through the BLUE LANCE website https://bluelance.com/, or send us an email via support@bluelance.com
1. FireEye Analysis
TEARDROP and BEACON Malware Used
Multiple SUNBURST samples have been recovered, delivering different payloads. In at least one instance the attackers deployed a previously unseen memory-only dropper we’ve dubbed TEARDROP to deploy Cobalt Strike BEACON.
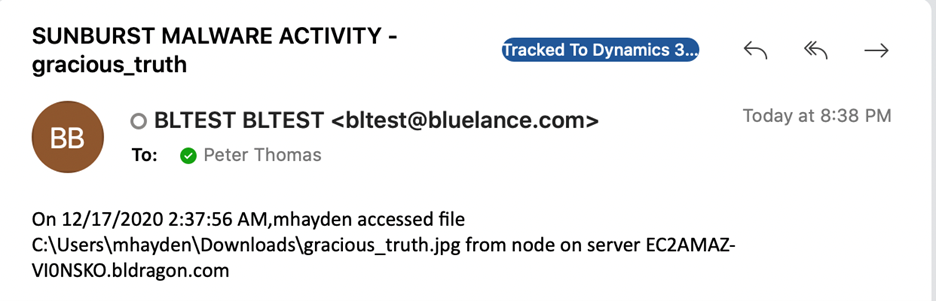
TEARDROP is a memory only dropper that runs as a service, spawns a thread and reads from the file “gracious_truth.jpg”, which likely has a fake JPG header. Next it checks that HKUSOFTWAREMicrosoftCTF exists, decodes an embedded payload using a custom rolling XOR algorithm and manually loads into memory an embedded payload using a custom PE-like file format. TEARDROP does not have code overlap with any previously seen malware. We believe that this was used to execute a customized Cobalt Strike BEACON.
Configure LT Auditor+ to track the file “gracious_truth.jpg”
Configure LT Auditor+ to notify security administrators, immediately in real time, of any access or activity of the file “gracious_truth.jpg”. This could be an indication of the malware being activated. An example of the real time alert generated by LT Auditor+ is displayed below
2. FireEye Recommendation
Organizations need to keep a lookout for access to the following file
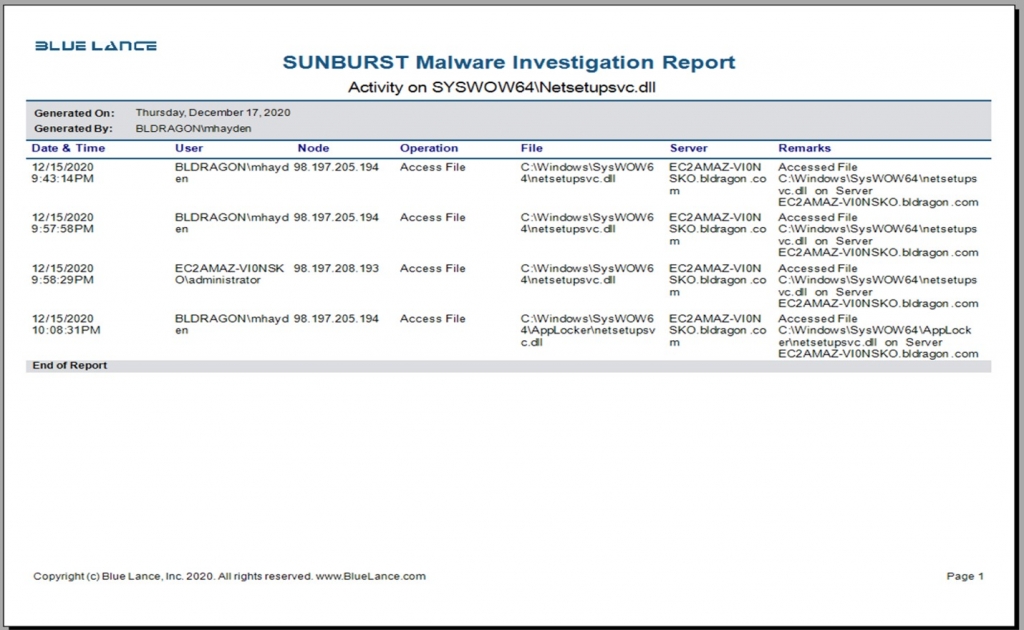
file-path*: “c:\Windows\SysWOW64\netsetupsvc.dll”
How to use LT Auditor+ to monitor and investigate access of c:windowssyswow64netsetupsvc.dll
Using LT Auditor+ a security analyst can be notified immediately if there has been any access to this file along with a detailed report to pinpoint when this file was accessed, by whom, and from where, along with all other activity on this file as shown below:
3. Fire Eye Recommendation
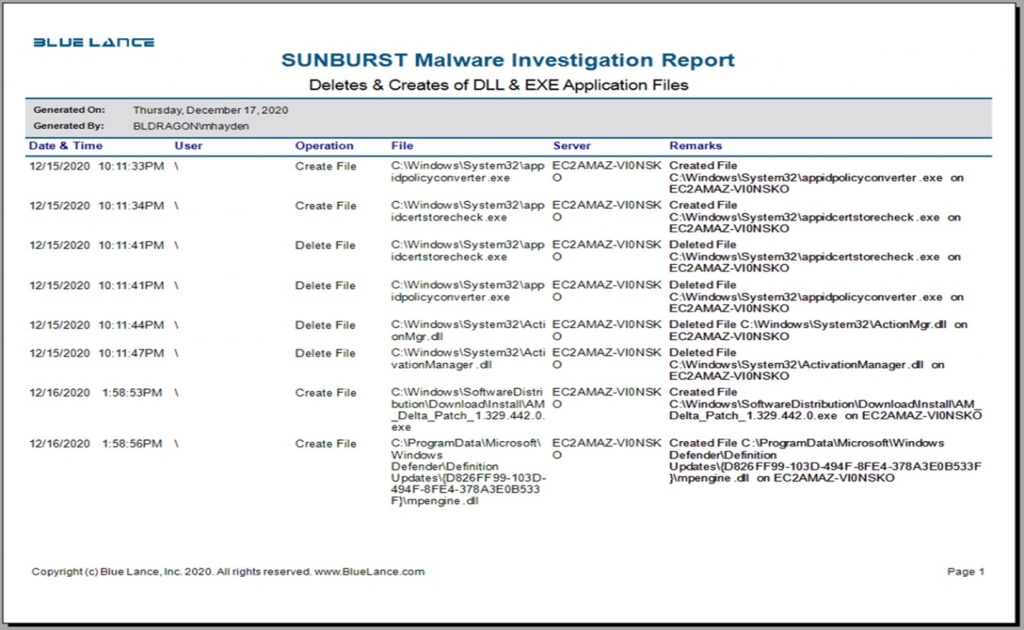
Defenders can examine logs for SMB sessions that show access to legitimate directories and follow a delete-create-execute-delete-create pattern in a short amount of time.
Use LT Auditor+ to meet this recommendation
LT Auditor+ can be configured to audit activity on all application files (.EXE and .DLL). A LT Auditor+ report showing this activity pattern and can be used to further the investigation. (This information is not accessed from the Windows event logs. (It is created by proprietary LT Auditor+ technology.)
4. Fire Eye Recommendation
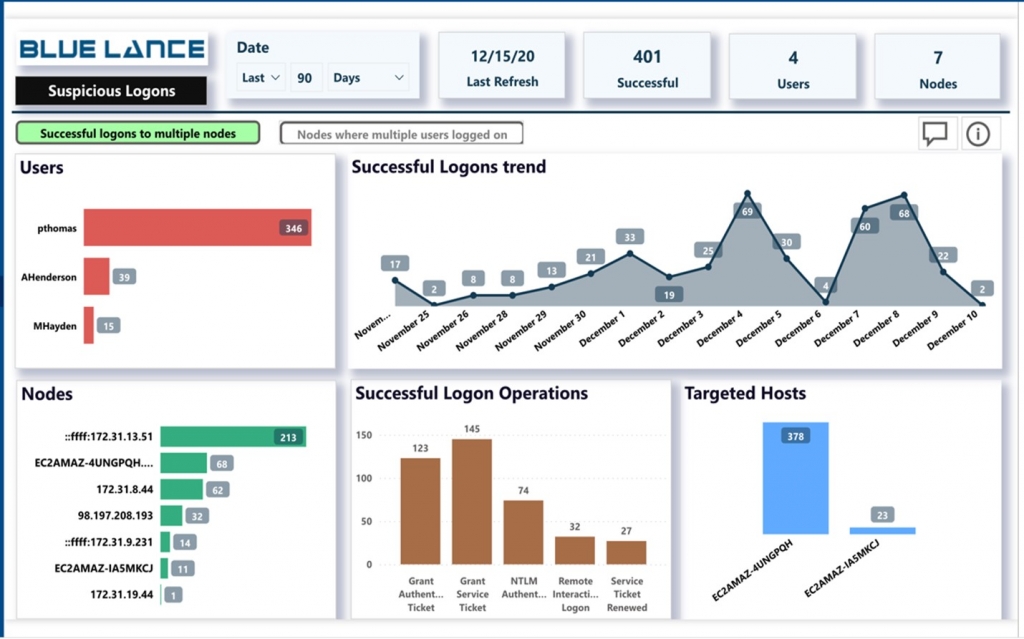
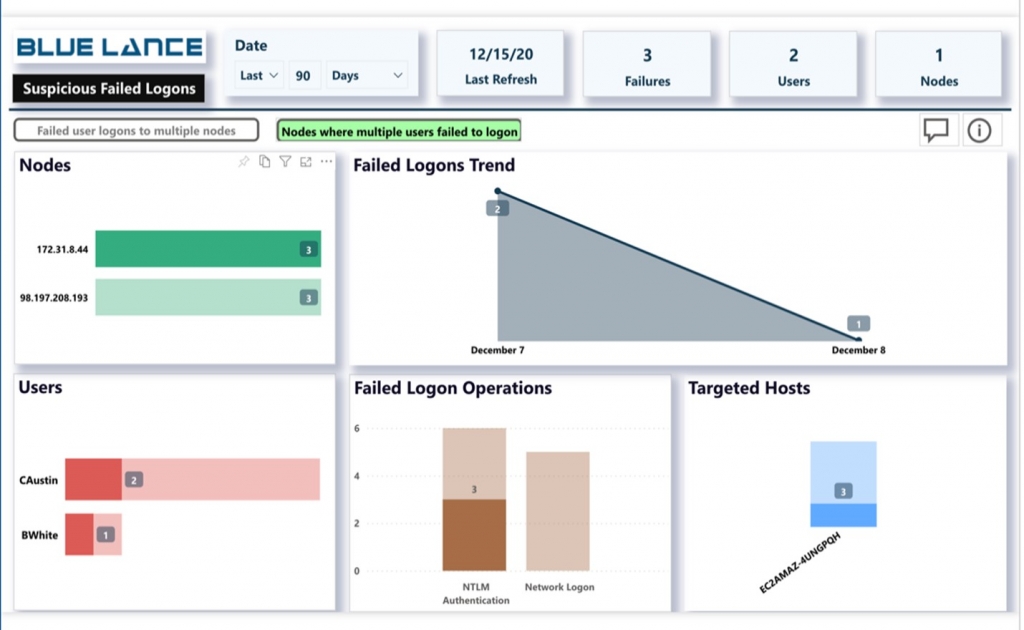
.. graph all logon activity and analyze systems displaying a one-to-many relationship between source systems and accounts. This will uncover any single system authenticating to multiple systems with multiple accounts, a relatively uncommon occurrence during normal business operations.
How to use LT Auditor+ to follow this recommendation
Use the “Suspicious Logons” and “Suspicious Failed to Logons” dashboards in LT Auditor+ to quickly identify users that use multiple systems to authenticate as well as identify multiple accounts authenticating via a single system as shown below:
And…
As previously mentioned, our helpdesk and engineering teams are ready to assist you with this security incident. Please do not hesitate to contact us at 1-800-856-BLUE (2583) in the US, or +1-713-255-4800 from outside the US. You may also connect with us via chat through the BLUE LANCE website https://bluelance.com/, or send us an email via support@bluelance.com
The BLUE LANCE Team
TO ARRANGE A TRIAL OF LT AUDITOR+ AT NO CHARGE:
Contact – Mikell Becker, VP, BLUE LANCE
mbecker@bluelance.com or call him directly at 713-255-4840


Leave A Comment