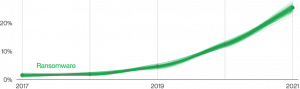
Ransomware attacks continue to increase every day. Cyber threats are hitting more businesses in the United States and worldwide. According to 2022 – Verizon Data Breach Investigation Report– “this year Ransomware has continued its upward trend with an almost 13% increase–a rise as big as the last five years combined (for a total of 25% this year)”.
Reducing the risk of a ransomware attack starts with reducing the attack surface of your exploitable IT network. Implementing a good IT security risk assessment is the first step towards reducing the attack surface of your network system. LT Auditor+ is the best IT security audit and compliance automation software for Microsoft Windows and OES networks. Our software provides you with the tools to identify and assess IT security risks of your Active Directory infrastructure.
Why is IT security risk assessment important?
Today every enterprise is vulnerable to ransomware attacks. It is critical to identify and remediate IT security risks to protect the business. LT Auditor+ provides you with intuitive, pre-built reports to easily identify critical vulnerabilities. Our IT security audit software is designed to help IT administrators reinforce their security controls to reduce the risk of ransomware.
Top 5 IT Security Risk Assessments for Active Directory
Implement the top 5 IT security risk assessments to identify risks within your Active Directory infrastructure.
1. Assess dormant privileged accounts
Privileged dormant accounts are one of the top vulnerabilities on your network. These accounts are coveted by ransomware attackers since they have total access to the IT infrastructure to inflict maximum damage. Dormant Privileged Accounts can be exploited because:
- Attackers use these forgotten accounts to perform unnoticed activities.
- Threat actors often use past employee credentials to illegally access the network.
- Past employees can sell their credentials to bad actors or use them to snoop, remove or destroy sensitive and/or competitive information.
The LT Auditor+ provides IT administrators with customizable reports to review all the dormant privileged accounts in your Active Directory so that they can be disabled.
2. Assess password age configuration vulnerability
Accounts with non-expiring passwords set the stage for brute-force and password spraying attacks and give attackers access to vast amounts of sensitive data, especially for accounts with admin access. Passwords that aren’t rotated also have a higher likelihood of showing up in breached password dumps. The following data points highlight the vulnerability of not changing passwords:
- Even after experiencing a data breach such as a man-in-the-middle attack or phishing attack, only 53% of IT security professionals say their organizations changed how passwords or protected corporate accounts were managed. (Yubico and Ponemon Institute)
- 45% of survey respondents did not change their passwords in the past year even after a breach had occurred. (LastPass)
- 85% of data breaches involved a human element such as phishing, stolen credentials, and human error. (Verizon)
- As of 2020, it’s estimated that there are more than 15 billion stolen credentials available to cybercrime actors on the dark web. (Forbes)
- Of passwords recovered from breaches in 2020, 60% of victims had reused at least one password across multiple platforms. (InfoSecurity)
LT Auditor+ arms your organization with the ability to detect all user accounts with passwords that never expire.
LT Auditor+ also gives you insights on “password not required” accounts and user accounts with password changes not allowed.
3. Assess user accounts with password reset privileges
Ensuring that only authorized users have privileges to reset passwords is vital in reducing your attack surface area. Unauthorized resets of account passwords often lead to account takeovers. LT Auditor+ identifies users with password reset privileges and makes it easy to validate access.
4. Assess granted group membership privileges
The ability to grant group membership poses significant risk when rights have been granted to unauthorized individuals — especially if the group has powerful privileges or access to sensitive information. Checking to ensure that only authorized accounts are granted this privilege reduces ransomware risk within your environment. LT Auditor+ Best Practice Panels display all users with Group Membership privileges and make it easy to validate authorization.
5. Access excessive privileges for users, groups, OU’s, and containers
A core tenet for hardening the Active Directory infrastructure is to follow the principle of least privileges. LT Auditor+ automatically lists all Active Directory objects that have been granted full rights/access to specific Active Directory resources. This allows you to quickly validate correct authorization.
Summary
Protecting your business against ransomware attacks starts with an IT security risk assessment of your information technology infrastructure. Learn from the top 5 security ransomware risk assessments for Active Directory to improve your IT security posture. LT Auditor+ is the solution of choice for IT administrators and cybersecurity experts to ASSESS, INVESTIGATE, and AUDIT Active Directory infrastructures.
Did you enjoy reading this article? Find more insightful learning from our latest white paper: How to Manage and Mitigate Ransomware Risk with LT Auditor+.












Leave A Comment