Knowing how to investigate ransomware risk is absolutely critical to maintaining a safe online presence in today’s fast-paced world. With unprecedented numbers of people conducting business online, there is a parallel and unfortunate trend showing a substantial increase in malicious activity. From cyberattacks to malware, organizations must be able to assess any security vulnerability before things go sideways in order to protect their assets, as well as their customers’ data and safety.
Speed is critical when ransomware attempts to strike. Swift and detailed identification of threats can enable incident responders to deploy a protection plan that will bolster cyber security and accelerates recovery time from any incident.
There are best practices to plan for, identify and recover from potential ransomware activity. Building a strong data security infrastructure that is responsive and adaptable helps to keep your organization functioning at its highest level, with top data security in place. Having an effective software that monitors suspicious activity is key.
Suspicious Events: Why It’s Important to Investigate Ransomware Risk
Early identification of suspicious activity and swift remediation of IT security risks can protect your organization. Without mitigating risk, you are leaving your business open to disruptive online attacks including threat actors who can demand you pay the ransom to resume normal operations. A ransomware attack can render your organization non-functional. Locked files, applications down, and organizational paralysis – the implication on day-to-day operations is endless.
Unfortunately, as the online world expands globally, these cyberattacks are becoming increasingly common. Unprotected organizations can be held “hostage” with demands of ransom payments to restore network operations. The impact of ransomware attacks is expensive and far-reaching.
To combat the rise in malicious activity, it is important to Identify ransomware investigation tools like LT Auditor+ to provide high-level risk mitigation for your company. LT Auditor + is a streamlined IT security audit system with extensive compliance automation for Microsoft Windows and OES networks. There are many ways LT Auditor+ works behind the scenes to identify your security vulnerability and prompt you to act before it’s too late. Here are the top 5:
Top 5 Security Risk Investigations within Your Active Directory – Be Alert.
The Investigate function of LT Auditor+ is an active, real-time malware protector that is consistently on the lookout for suspicious activities and can promptly alert you to a ransomware attack vulnerability. Here are some of the red flags our software identifies during IT security audits, helping to keep you safe from malware and data breach:
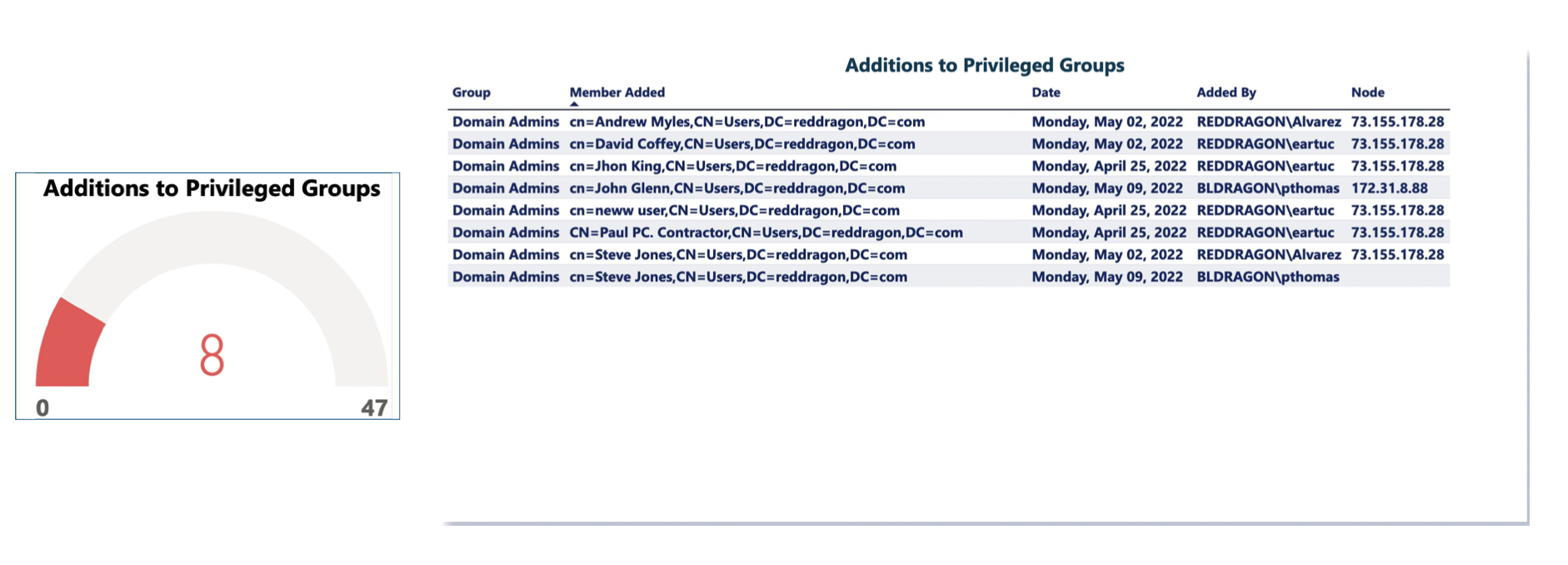
1. Privilege Escalation
In any IT organization, there are certain protected groups such as “Domain Admins” who have complete control of Active Directory Resources. LT Auditor + detects any changes to these powerful groups, which can be indicative of a breach in security. By watching in real-time, your company IT admin list remains secure, and your data integrity, tightly protected.
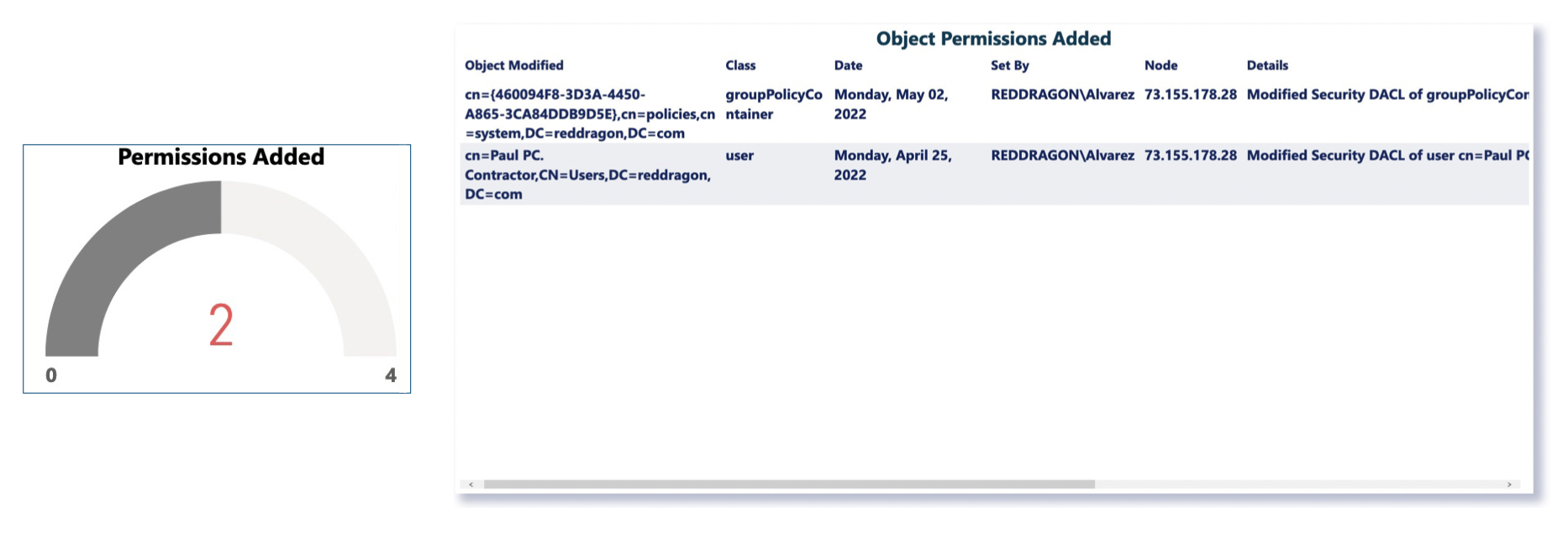
2. Changes in Privilege to Active Directory Objects
By closely watching the privilege status of other objects in the active directory, LT Auditor+ ensures that ransomware attackers are not slowly escalating their privilege to gain access and control of your system.
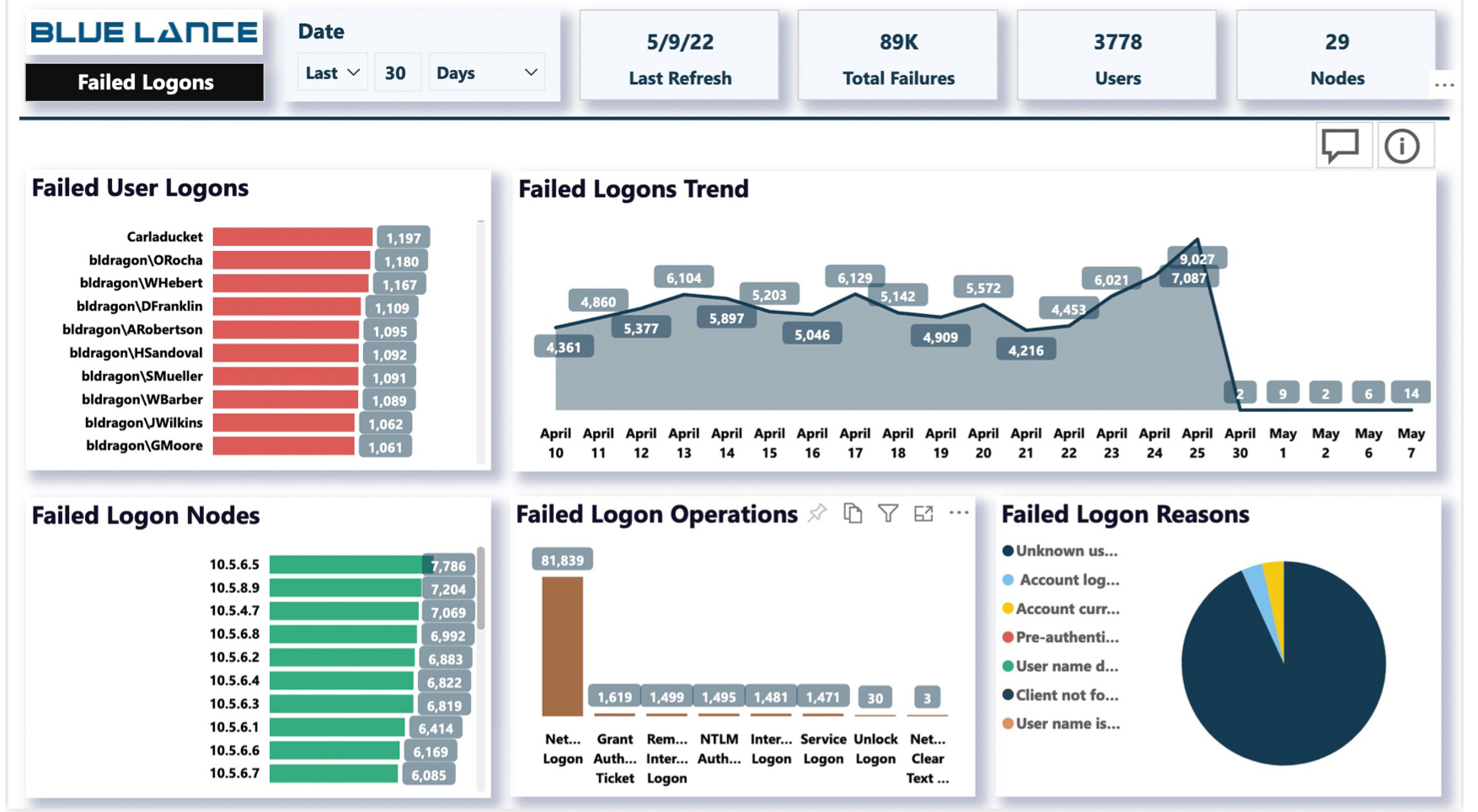
3. Excessive and Suspicious Logon Practices
Repeated and unsuccessful logon attempts can indicate a cybersecurity compromise. Within LT auditor+, a panel specifically monitors logons and emerging trends, raising the alert status when a deeper investigation is needed.
A security investigation can quickly identify a pattern of attack, and trigger safeguards that prohibit massive password breaches. The LT auditor+ system monitors all system logon failures and institutes a fast protection plan before a ransomware attack occurs. LT Auditor+ will investigate repeated account lockouts and create easy-to-understand visuals that show attempts over time. Suspicious, repeated lockouts will be actively investigated, and safeguards put in place to protect systems from malicious activity.
Certain patterns of logons, even those that are successful, can indicate malware infection. If for some reason a user’s credentials have been compromised, LT Auditor+ recognizes suspicious lateral movements within an organization and can raise alert for a ransomware attack. Comprehensive logon analysis, on an ongoing basis is a key to protecting an organization for cyberattack.
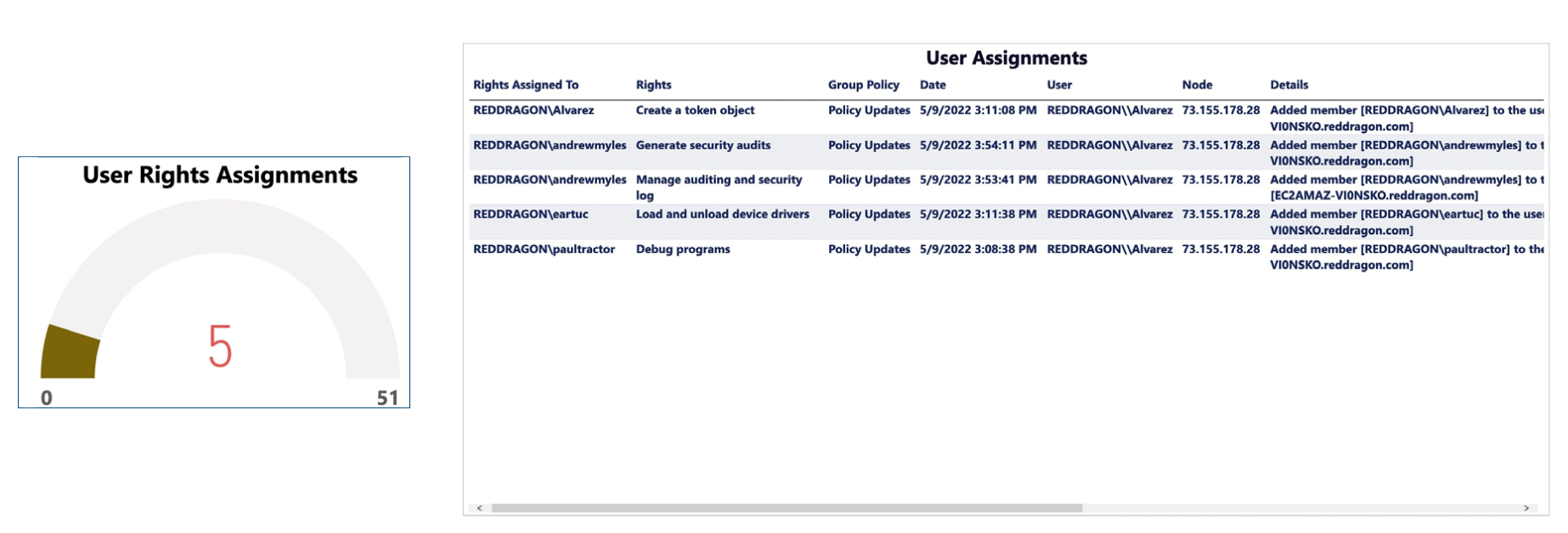
4. User Rights Assignments
Every network has various user rights’ assignment that delineate system privilege and task assignment. Careful analysis of the assignments by LT Auditor+ ensure that only personnel with rightful access are performing sensitive tasks within the network.
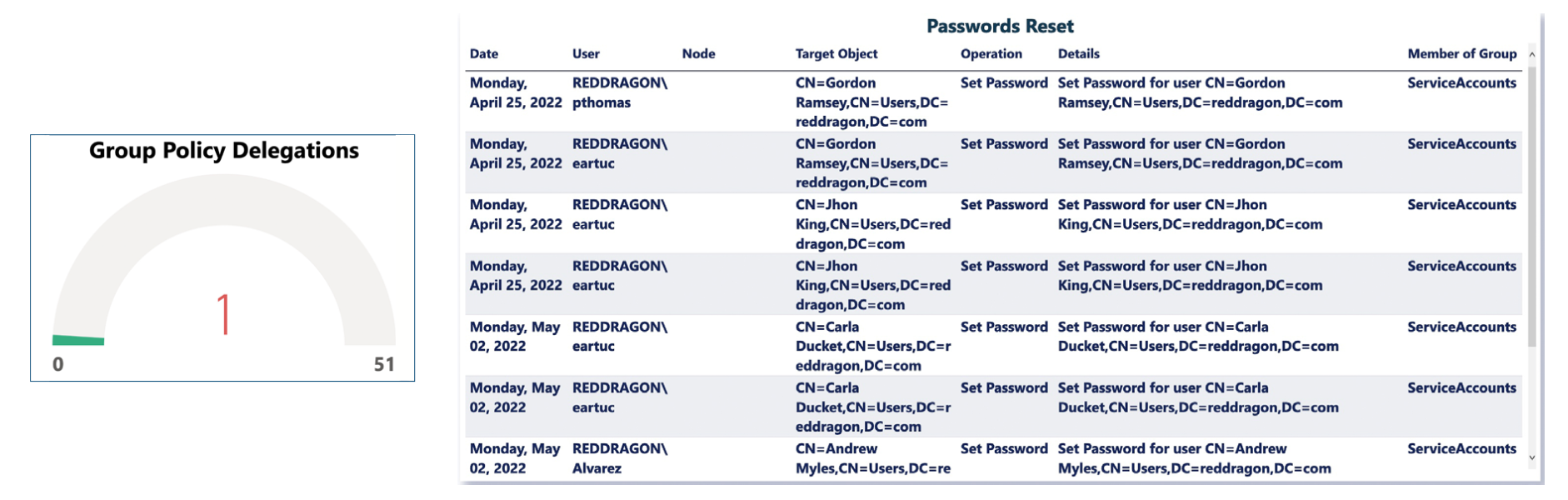
5. Group Policy Delegations
In daily operations, admins delegate rights to verified users. In a ransomware attack, unverified and dangerous access can disrupt daily operations. LT Auditor+ closely monitors the entire system, making sure only those verified personnel are accessing certain identified groups.
Summary: A Proactive Plan to Minimize Ransomware Attacks
Keeping a company’s IT system safe and protected is a complex process. Rigorous, high-level monitoring with a comprehensive software program like LT Auditor+ is a foundational and crucial step in safeguarding operating systems and data.
Having a proactive approach to investigate ransomware risk helps to maintain smooth operations and ensure ransomware attacks are minimized. There are concrete steps you can take to protect data, tighten online security, and develop an incident response plan that will go a long way towards stopping malicious activity.
LT Auditor+ is an integral part of your threat response team. Our software helps clients quickly contain and investigate threats, coordinating a tactical, effective response to each incident. We are on your side when it comes to fighting ransomware.
Learn more about what you can do today to protect your enterprise by downloading our free resource: How to Manage and Mitigate Ransomware Risk with LT Auditor+







Get Social