The protection of data and information assets is a key, ongoing focus for organizations around the world. Using encryption technology, limitations to access, and various high-level efforts, as quickly as organizations put a security practice in place, bad actors are evolving in their pressure tactics to infiltrate the system. Ransomware is an evolving tool of cybercriminals and a primary method of extorting payments from companies who are unprotected. Knowing how to audit ransomware risk should be a pivotal prong of multi-faceted and comprehensive protection of assets.
Ransomware is a malicious software or type of malware that blocks access to data, encrypts it, or threatens to publish data unless the victim of the cyberattack pays ransom. Unfortunately, cybercriminals continue to evolve their attack strategies and pressure tactics, causing more disruptions and negatively impacting businesses across the globe. Understanding how to audit ransomware risk is key to securing an operating system, a business, and a community.
Ransomware attacks are generally becoming more complex causing almost every organization to perform vulnerability assessments and regular audits to ensure that their data security is impenetrable. Companies need the highest level of security controls available to ensure continuous operational safety and security, as well as data protection.
Here we will discuss why it is important to audit ransomware risk and how LT+ auditor can help.
Why it is Important to Audit Ransomware Risk
Ransomware is a top area of risk that audit departments need to monitor closely. More than ever before, increasingly sophisticated attacks are leading to higher costs- both in the ransom demanded and in the recovery process for businesses. Companies can experience unexpected downtimes, increases in tech-related costs and high demand ransoms.
Any organization should assume that they can be targeted in a ransomware attack and should develop a comprehensive prevention plan. Regular audits, both internal and external, can assist in keeping data breaches to a minimum and work to safeguard systems. Penetration testing, vulnerability assessments and audit reports give companies significant insight into important areas of potential threat. Any vulnerabilities must be quickly corrected.
Malicious actors have realized that by threatening to release personal data, they can demand higher ransoms in these malware attacks. In general, government dissuades organizations from paying ransoms, fearing an increase in this type of activity. For companies, cybersecurity awareness training along with a highly developed type of security audit such as LT+ auditor, can go a long way in keeping information systems intact and smoothly functioning.
Top 5 Security Risk Audits for Active Directory
The Audit Function of LT+ Auditor implements a sophisticated set of activities to verify and document users, networks, and also monitor applications. The data ensues that configurations and settings are secure and not exploitable by a ransomware attack. Here are some of the top audits associated with LT+ Auditor:
-
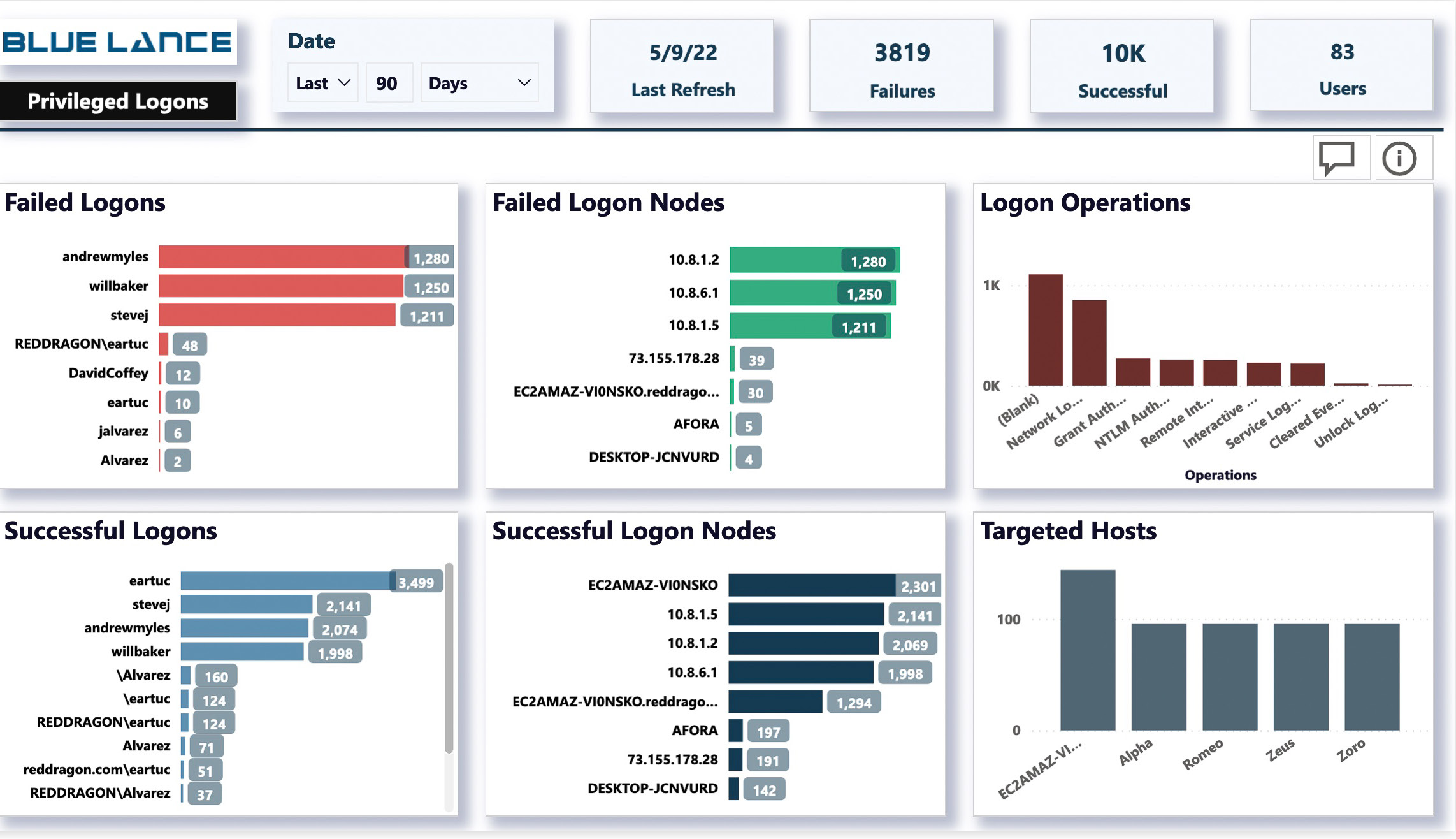
Privileged User Activity
Privileged user accounts are a frequent target of malicious actors trying to gain access to high-level servers or databases. Using malware, viruses or phishing attacks, privileged user accounts are the gateway for many ransomware breaches. LT+ Auditor carefully assesses privileged user activity to ensure that malicious activity is quickly halted.
-
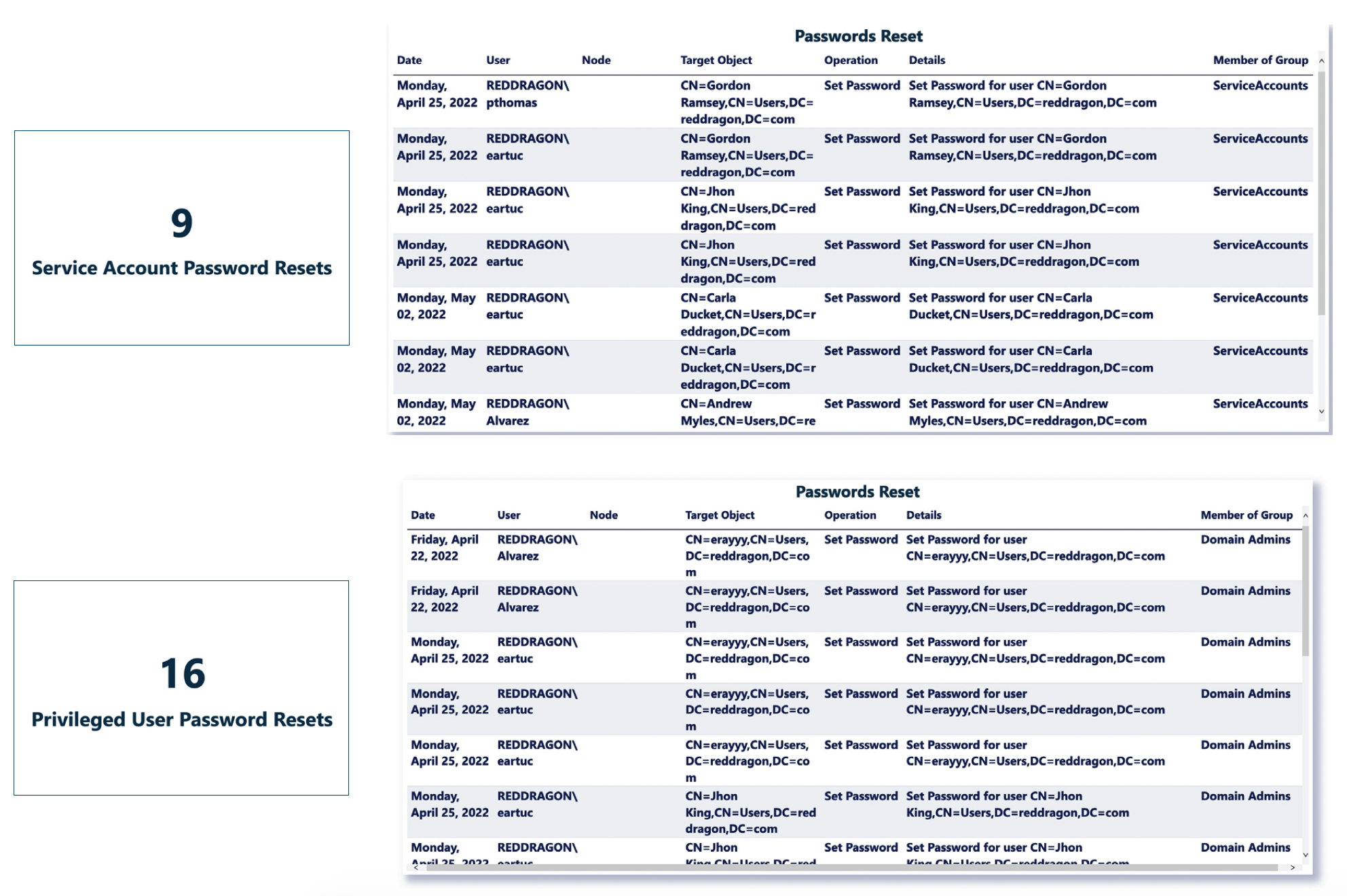
Password Changes To Privileged and Service Accounts
Strict password policy control and tightly monitored multifactor authentication processes are integral to keeping enterprise accounts secure. Any changes requested, especially to privileged accounts, must be closely audited to ensure only authorized access.
-
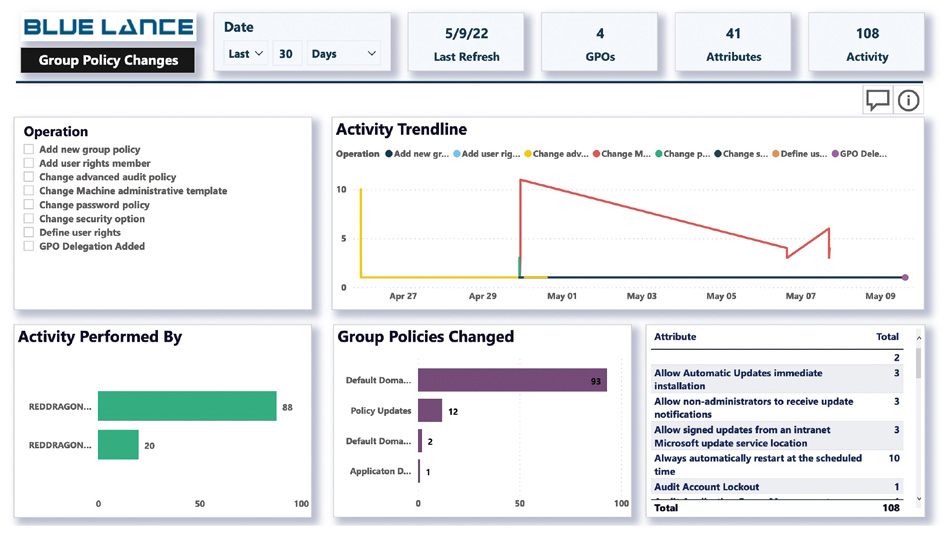
Group Policy Changes
The Group Policy Changes Panel integral to LT+ Auditor is a highly effective, easy-to-understand panel to audit all changes to Group Policies in a time-saving manner. By auditing changes, the organization limits hostile access, ensures security compliance, and increases safeguards surrounding accounts that are especially vulnerable to ransomware threats.
-
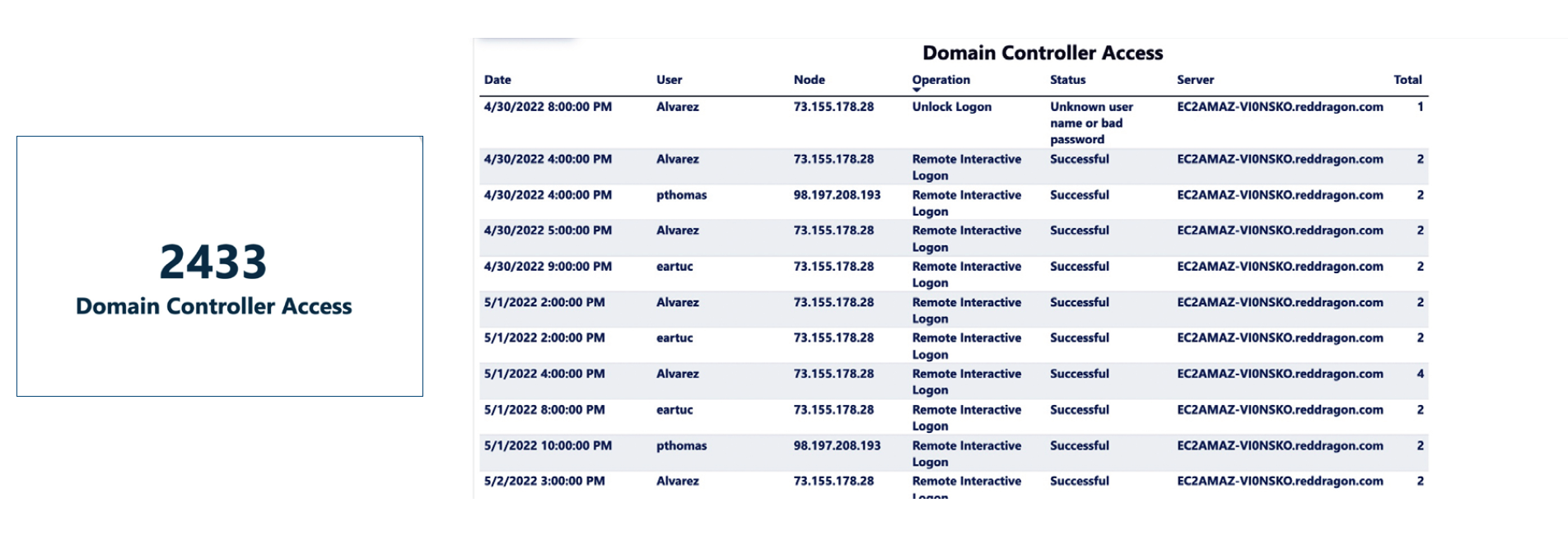
Domain Controller Access
The physical storage for the Active Directory database is housed within the Domain Controllers. They also help to manage servers, workstations, users, and all applications. It is absolutely critical to audit all direct access, including remote desktop access(RDP) and interactive logons to confirm only authorized activity.
If a malicious user gains access to the Domain Controller, everything in the Active Directory database is considered compromised. As with any intrusion access, the far-reaching implications of this type of attack are extremely serious. LT+ Auditor protects against unauthorized Domain Controller access and helps keep data systems safe and secure.
-
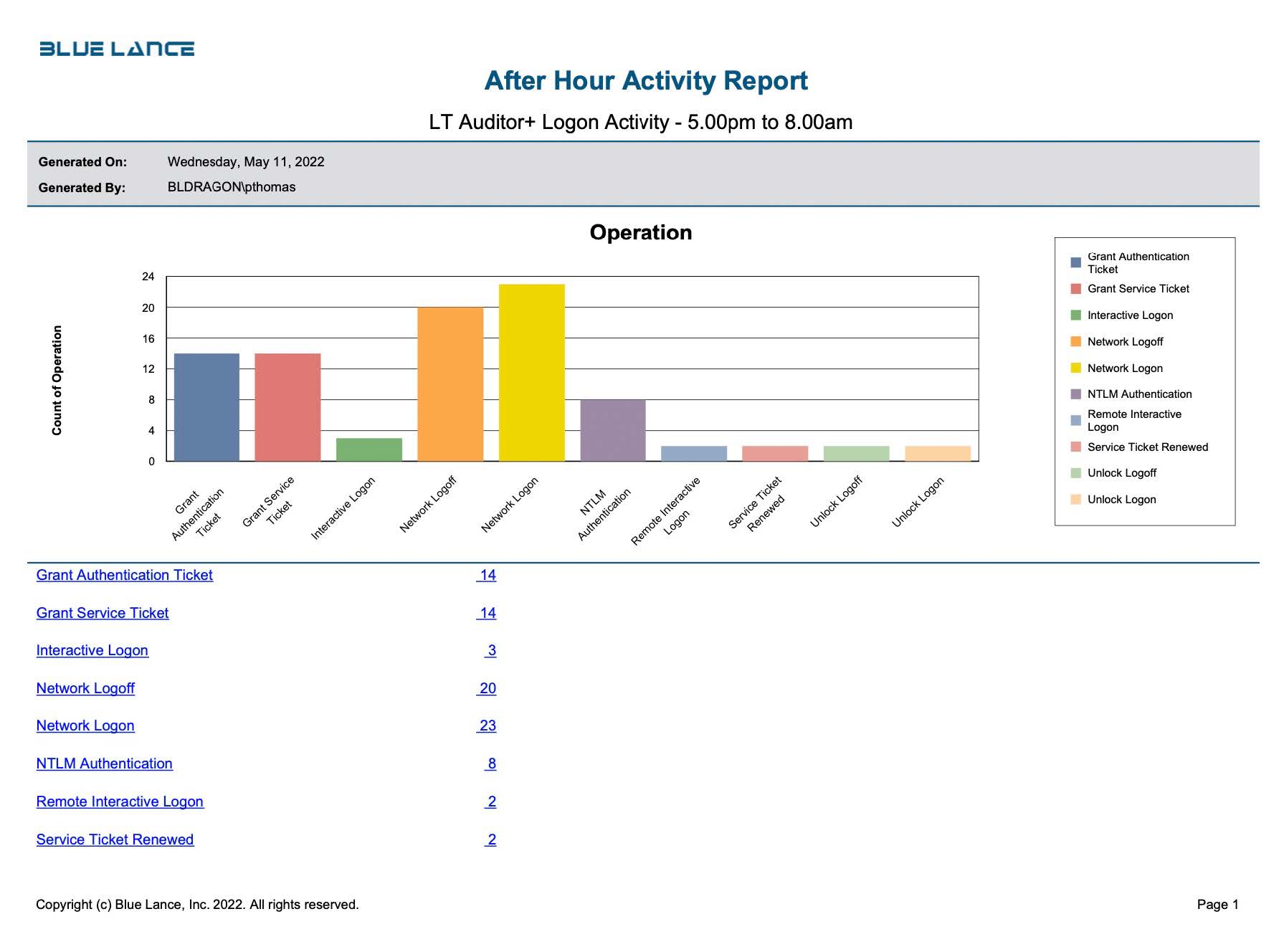
After Hours Activity
It is important to review network authentication during and after business hours. By auditing afterhours activity, any suspicious events scan be quickly reported, researched, and potentially interrupted. Any afterhours unauthorized activity is a red flag for malware action and must be investigated. LT+ Auditor can initiate an incident response 24/7 and minimize the damage of a ransomware attack as soon as it is detected.
Summary: The Importance of Audit Defenses for Ransomware Risk
Unfortunately, ransomware attacks are far too common today. No industry is completely shielded, with attacks occurring in companies big and small. Ultimately, any device connected to the internet is at risk of ransomware attack. Understanding the prevalence of ransomware attacks, and knowing what to do before they occur, is an important step keeping data secure.
Every organization needs an effective ransomware response plan that includes strong mitigation, open communication, recovery strategy and resolution steps. Risk assessment and security audits are two key components of successful mitigation.







Get Social