Access control is used to govern user access to shared resources for security purposes. Active Directory access control is administered at the object level by setting different levels of access, or permissions, to objects. Some of the types of permissions that can be given to any object are:
- Full Control – complete access
- Write
- Read
- No Access
- Create Child Objects
- Delete Child Objects
- Any many more
The elements that define access control permissions on Active Directory (AD) objects include security descriptors, object inheritance, and user authentication. The security descriptor contains the following:
- A Discretionary Access Control List (DACL), which comprises Access Control Entries (ACEs) that indicate which users and groups have been explicitly allowed or denied a specific type of access to the object. The ACE may specify which operations they can perform and whether or not they can create child objects or define private or extended access rights.
- A System Access Control List (SACL), which identifies the types of actions that generate an audit log entry. The ACEs in this list indicate a user or group, the type of access attempted, and whether success or failure or both will generate the audit.
- A Security Identifier (SID) to identify the owner of the object. Ownership implies the right to modify the DACL.
LT Auditor+ 2013 can scan for all types of directory objects and report the security permissions (DACLs) assigned or inherited. This information is valuable to ensure that security administrators document and validate who should and should not have permissions to resources in the directory.
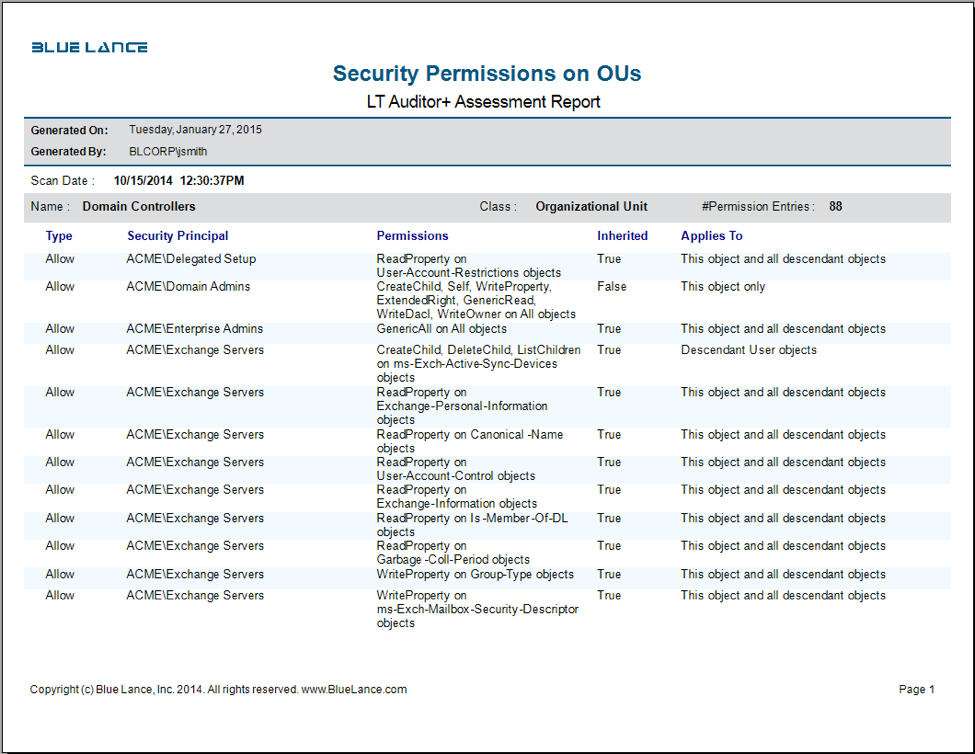
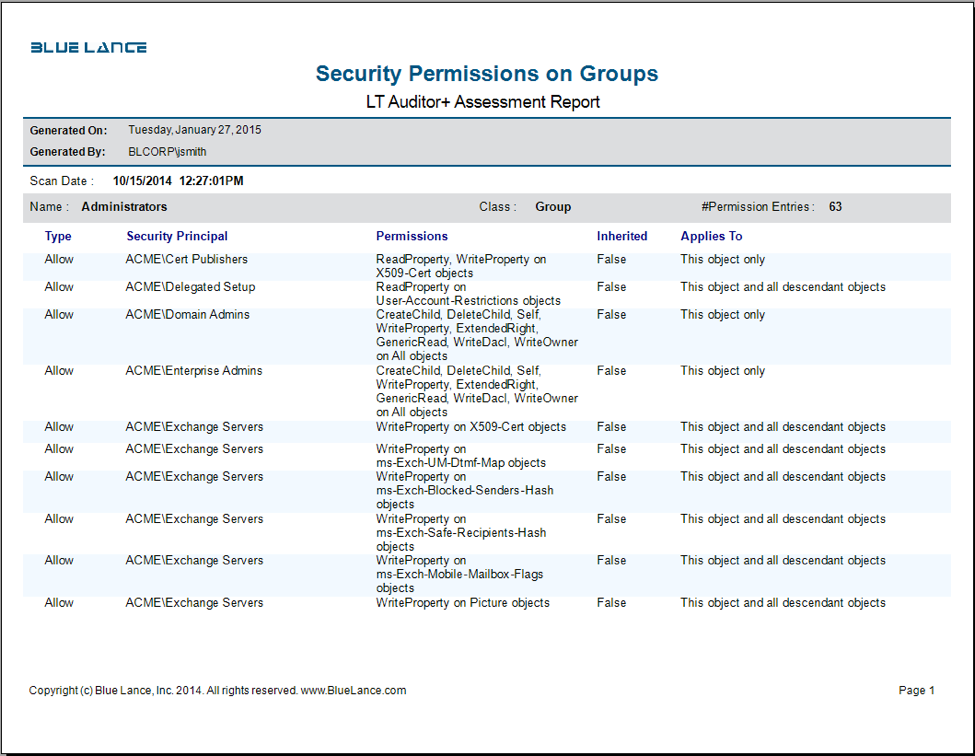
By default, DACLs and SACLs are associated with every Active Directory object, which reduces attacks to your network by malicious users or any accidental mistakes made by domain users. However, if a malicious user obtains a user name and password of any account with administrative credentials to Active Directory, your forest will be vulnerable to attack. For this reason, it is critical to monitor changes to permissions within the directory. LT Auditor+ provides real-time notification when any change is made to DACLs in the directory.
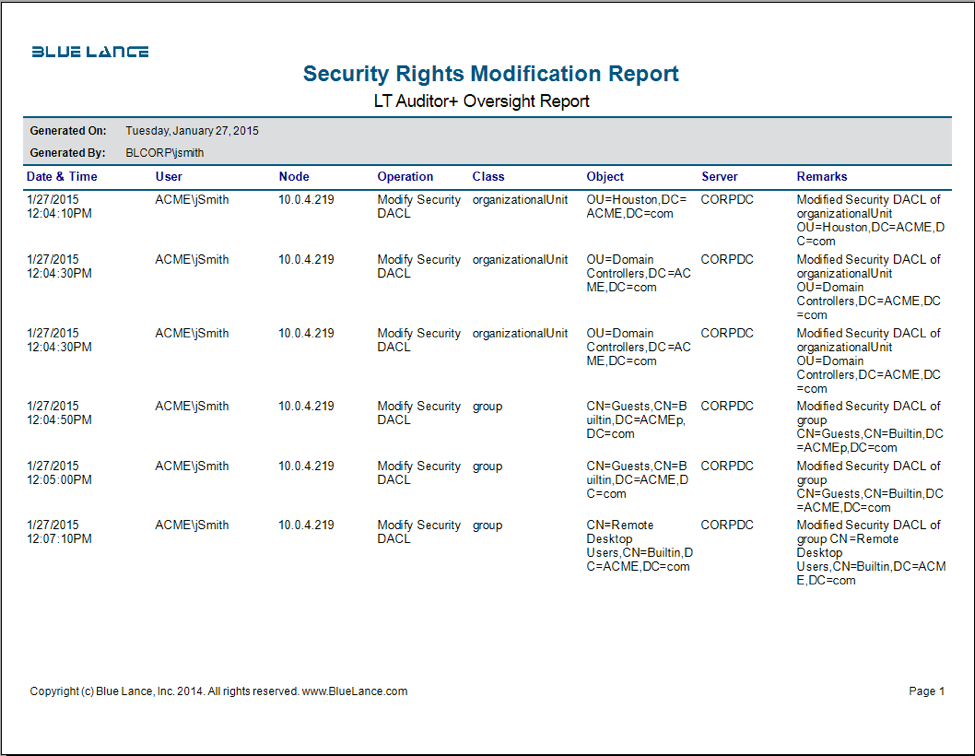
By default, Active Directory objects inherit ACEs from the security descriptor located in their parent container object. Inheritance enables the access control information defined at a container object in Active Directory to apply to the security descriptors of any subordinate objects, including other containers and their objects. Changes to inherited permissions should be closely monitored, and LT Auditor+ can provide details on who modified DACLs on Active Directory objects.
Microsoft recommends several best practices with regards to changing and assigning AD permissions:
- Avoid changing the default permissions on Active Directory objects, as changing default permissions could cause unexpected access problems or reduce security.
- Avoid granting Full Control permissions over an object or organizational unit since granting someone Full Control allows the user to take ownership of an object and modify the permissions on it. If someone has Full Control on a container, then he or she can Take Ownership of, and have Full Control over, all objects in that container. As far as possible, instead of allowing Full Control, give only the permissions needed by the user.
- Minimize the number of access control entries that apply to child objects. When using the Apply Onto option to control inheritance, be aware that not only will the specified objects inherit that access control entry (ACE) but all child objects will also receive a copy of that ACE. If there are enough objects that will get copies of this ACE, then that increased amount of data can cause performance problems on your network.
- When possible, assign the same set of permissions to multiple objects. Access control lists (ACLs) feature single-instancing: If multiple objects have identical access control lists (ACLs), then Active Directory will only store one instance of the ACL.
- When possible, assign access rights on a broad level rather than assigning individual user rights:
- Minimize the number of access control entries to improve performance.
- Allow “Read All Properties” or “Write All Properties” rather than individual properties.
- Allow Read or Write access to property sets rather than individual properties.
A property set is a collection of attributes. For example, the Personal Information property set includes the attribute’s address, personal title, and so on. By setting access on the property set, you have automatically set access on all the attributes contained in that property set. - Allow “Create All Child Objects” or “Delete All Child Objects,” rather than specifying individual child objects.
- Allow “All Extended Rights” rather than allowing the individual extended rights.
- Allow “All Validated Rights” rather than allowing the individual validated rights.
- Whenever possible, assign permissions to groups rather than users. Use of groups to delegate authority over the directory is more efficient. If one set of users needs Read permissions and another set of users needs Change permissions, then create one group for each set of users and assign the permission to the group. If multiple global groups need the same access, create a local group containing the global groups and assign permissions to the local group.
Benefits of scanning and monitoring for AD permissions with LT Auditor+
- Comply with principals of least privilege and “need to know” by identifying sensitive objects with excessive rights for remediation.
- Use real-time notification when permissions on important AD objects are changed, enabling security administrators to quickly check for authorization and validation.
- Meet compliance requirements from SOX, PCI-DSS, HIPAA, FFIEC, and NIST by demonstrating vigilance in scanning for such activity.
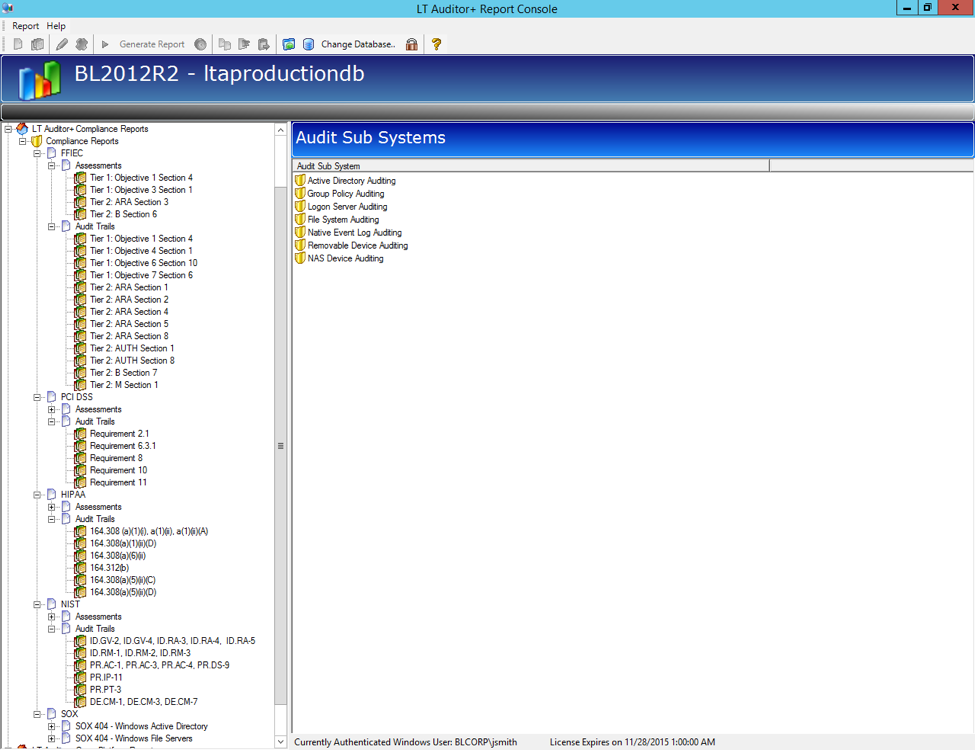
About LT Auditor+
LT Auditor+ is a suite of applications that provide real-time monitoring and auditing of Windows Active Directory and Windows Servers changes. The application audits-tracks-reports on Windows Active Directory, Windows Workstations Logon/Logoff, Windows File Servers, and Member Servers to help meet security, audit, and compliance demands or requirements. Track authorized/unauthorized access of users’ Logon/Logoff, GPO, Groups, Computer, OU, and DNS server changes with over 300 detailed event-specific reports and real-time email alerts. Reports generation can be automated, scheduled, and exported to multiple formats like PDF, Excel, HTML, and CSV that further assist with a forensic investigation.







Leave A Comment