User account lockouts in Active Directory occur for a variety of reasons, and often the challenge is to determine the Windows node and user causing the lockout so as to resolve the issue. Account lockouts can be a frustrating experience for users, a nightmare for network administrators, and a cause for concern for security administrators. LT Auditor+ can provide detailed activity reports that identify the machines where account lockout activity occurred. Additionally, the login activity that caused the lockout is also available, giving investigators a complete picture of where and how accounts are getting locked out.
Microsoft uses two types of protocols for authentication:
- Kerberos authentication (default)
- NT LAN Manager (NTLM) authentication
A brief explanation of these protocols will provide more clarity on understanding the LT Auditor+ login activity associated with tracking account lockouts.
Kerberos authentication: Kerberos authentication, which is the default protocol, provides a mechanism for mutual authentication between a client and a server on Windows Active Directory networks. Kerberos comprises the Key Distribution Center (KDC), the client user, and the server. The KDC is installed on a Windows AD Domain Controller and authenticates a user using the Authentication Service (AS) and the Ticket-Granting Service (TGS). All access by users to resources on the network requires a valid security token or ticket granted by the KDC. When Kerberos authentication fails, LT Auditor+ is able to capture this information on the domain controller. The following report is an example of details provided:
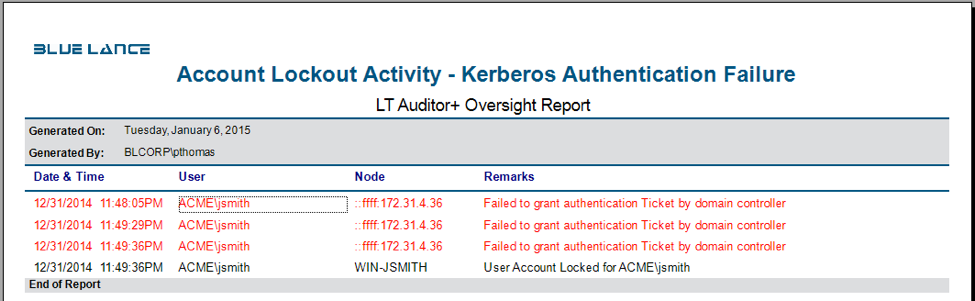
The report shows how user jsmith’s account was locked after multiple login attempts from the workstation node 172.31.4.36. The login failures reported were caused by pre-authentication Kerberos login failure identifying the IP address of the node which caused the failure.
NTLM Authentication: NTLM protocol uses a challenge response methodology in which the client sends the username to a Windows server. The server generates and sends a challenge to the client, which the client encrypts using the user’s password. This encrypted message is sent back as a response to the server. For local user accounts, the server validates a user’s response by looking into the Security Account Manager (SAM), and for domain accounts the server forwards the response to a domain controller for validation based on the group policy configured for user accounts. When NTLM authentication fails, LT Auditor+ is able to capture this information on the domain controller. The following report is an example of details provided:
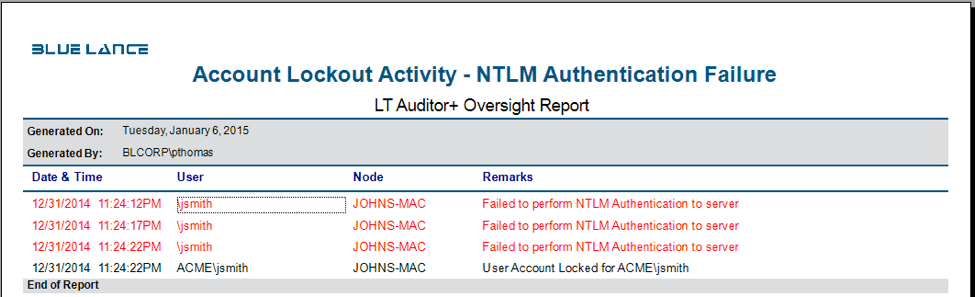
The report shows how the user jsmith’s account was locked after multiple login attempts from the workstation ‘JOHNS-MAC.’ The login failures reported were caused by NTLM authentication failure identifying the workstation node that caused the failure.
Benefits of tracking and monitoring account lockout activity with LT Auditor+
- Identify account lockouts in real time to ensure that a dictionary attack is not being attempted on the network. Email alerts can be triggered only when specified powerful accounts are locked out.
- Troubleshoot account lockouts to find causes of account lockouts and prevent loss of productivity, end user frustration, and improve incident response with high-quality reports.
- Meet compliance requirements from SOX, PCI-DSS, HIPAA, FFIEC, and NIST by comprehensively tracking and monitoring account lockout activity.
- Monitor access by privileged user accounts for compliance and accountability and get real-time notification if any of these user accounts get locked out.
About LT Auditor+
LT Auditor+ is a suite of applications that provide real-time monitoring and auditing of Windows Active Directory and Windows Servers changes. The application audits-tracks-reports on Windows Active Directory, Windows Workstations Logon/Logoff, Windows File Servers, and Member Servers to help meet security, audit, and compliance demands or requirements. Track authorized/unauthorized access of users’ Logon/Logoff, GPO, Groups, Computer, OU, and DNS server changes with over 300 detailed event-specific reports and real-time email alerts. Reports generation can be automated, scheduled, and exported to multiple formats like PDF, Excel, HTML, and CSV that further assist with a forensic investigation.







Leave A Comment