Active Directory (AD) has two types of groups called Security and Distribution. Distribution groups are used for distribution lists in Exchange and cannot be assigned permissions or rights. Security groups are used for assigning permissions and rights and can also be used for distribution lists.
As security groups are used to control access permissions to resources on the network, it is important for security administrators to:
- Get signoff on members of security groups who have access to sensitive and critical information.
- Make sure that new members added or removed from important groups have been formally authorized by management.
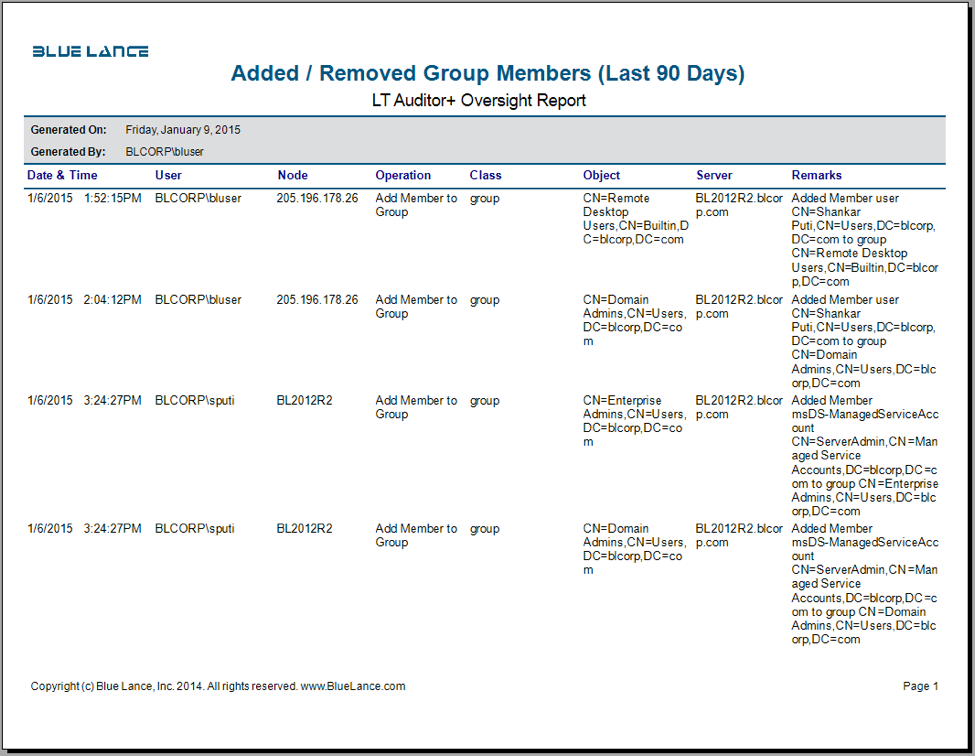
LT Auditor+ can scan and generate detailed reports on members of sensitive and powerful groups providing security administrators the information needed to validate these memberships with business or data owners. LT Auditor+ can also provide real-time notification along with reports on group memberships added or removed in the Active Directory environment.
Within Active Directory there are built-in groups that have very high privileges, namely:
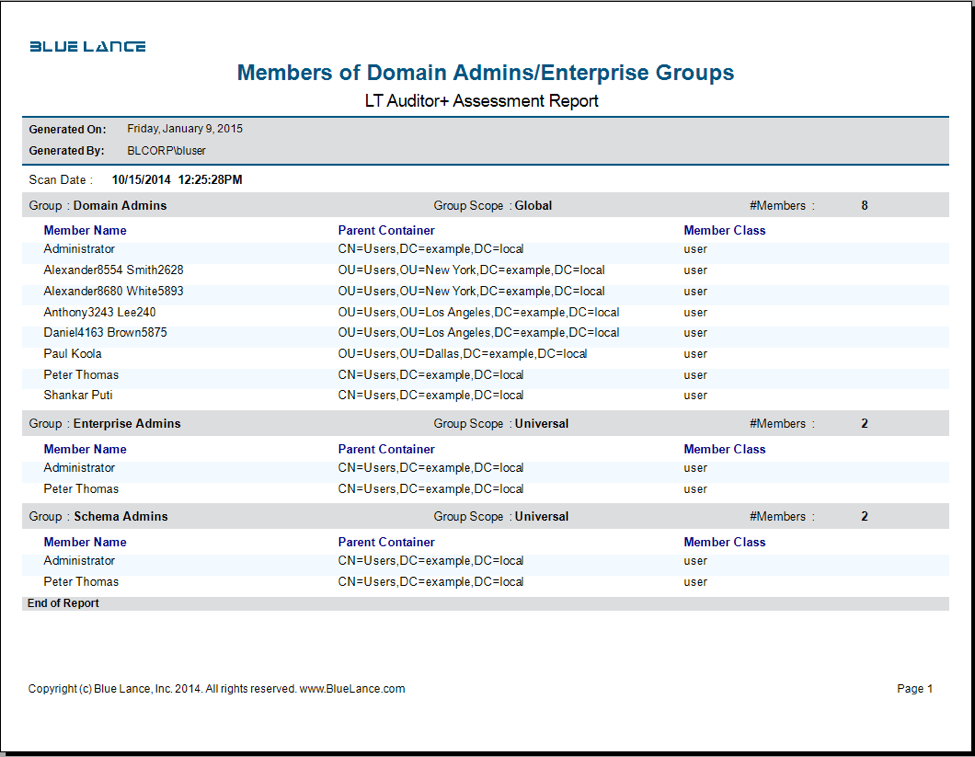
- Enterprise Admins (EA) is a group that exists only in the forest root domain and is granted rights and permissions that allow them to implement forest-wide changes such as adding or removing domains, establishing forest trusts, or raising forest functional levels.
- Domain Admins (DA) is a group that exists for each domain in the forest. DAs are “all-powerful” within their domains, which includes all Windows computers that connect to the domain.
- Built-in Administrators (BA) is a group that exists for every Window machine and is the group into which DAs and EAs are nested. This group is granted many of the direct rights and permissions in the directory and on domain controllers. The Administrators group for a domain has no privileges on member servers or on workstations, but it is via membership in the computers’ local Administrators group that local privilege is granted.
- Schema Admins (SA) is a group that exists only in the forest root domain and is the only group that can modify the Active Directory schema that define type classes and attributes.
- A member of any of these AD groups has extraordinary privileges, and every organization must track and record the current memberships as well monitor when new memberships are assigned. LT Auditor+ provides security administrators with complete visibility of current memberships of powerful groups and provides clear accountability by recording who made a user a member of any of these groups.
The following reports demonstrate the clarity of how LT Auditor+ can scan, monitor, and track group memberships in Active Directory.
Membership of Powerful AD groups
Users added or removed from powerful groups
Benefits of scanning and monitoring for group memberships with LT Auditor+
- Complies with principals of least privilege and “need to know” by identifying users with memberships to groups with unauthorized access to resources.
- Secures Domain Controllers and other applications against attacks by monitoring in real-time when users are added to powerful enabling security administrators to check for authorization and validation.
- Reduces the Active Directory attack surface by providing information about privileged accounts and groups and proactively monitoring activity on members of these groups.
- Meets compliance requirements from SOX, PCI-DSS, HIPAA, FFIEC, and NIST by demonstrating vigilance in scanning for such activity.
About LT Auditor+
LT Auditor+ is a suite of applications that provide real-time monitoring and auditing of Windows Active Directory and Windows Servers changes. The application audits-tracks-reports on Windows Active Directory, Windows Workstations Logon/Logoff, Windows File Servers, and Member Servers to help meet security, audit, and compliance demands or requirements. Track authorized/unauthorized access of users’ Logon/Logoff, GPO, Groups, Computer, OU, and DNS server changes with over 300 detailed event-specific reports and real-time email alerts. Reports generation can be automated, scheduled, and exported to multiple formats like PDF, Excel, HTML, and CSV that further assist with a forensic investigation.







Leave A Comment