What checks can be run to understand why LT Auditor+ is not auditing File Activity on a Windows Server?
If LT Auditor+ is not auditing files and folders here are checks that can be conducted to detect the problem.
- Check the SACL policies on the local server
- Check the LT Auditor+ File Filter (FSA) policies
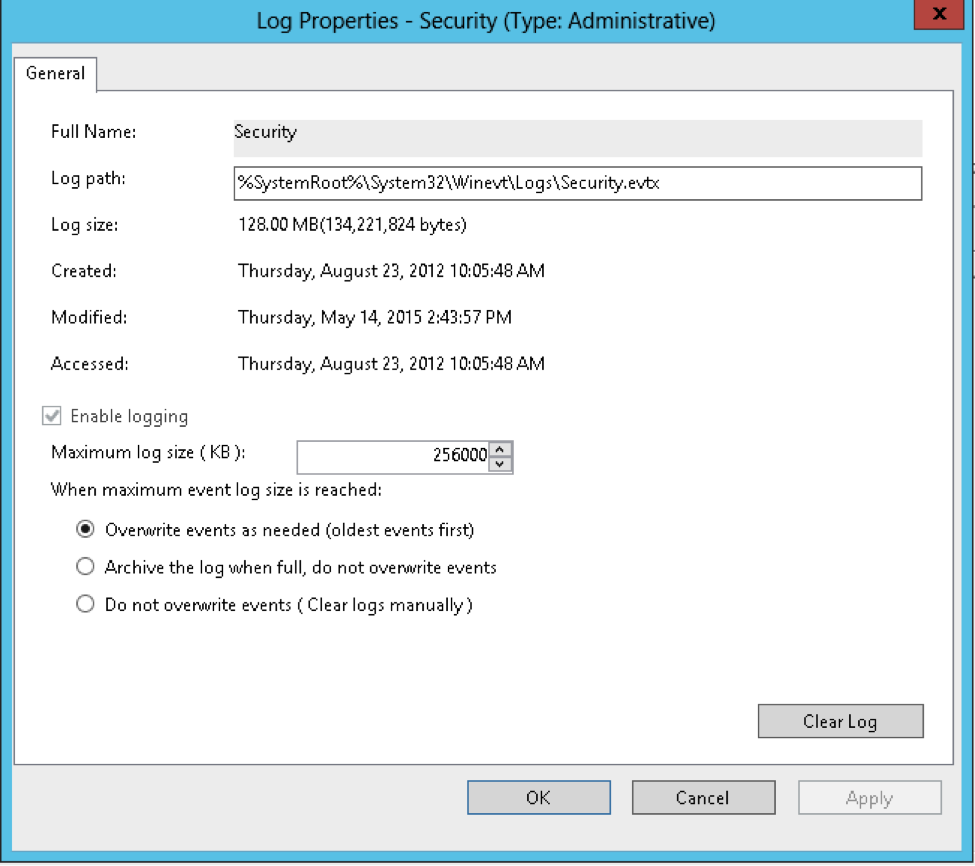
- Check the size of the Windows Security Log
Checking SACL Policies on a Windows Server
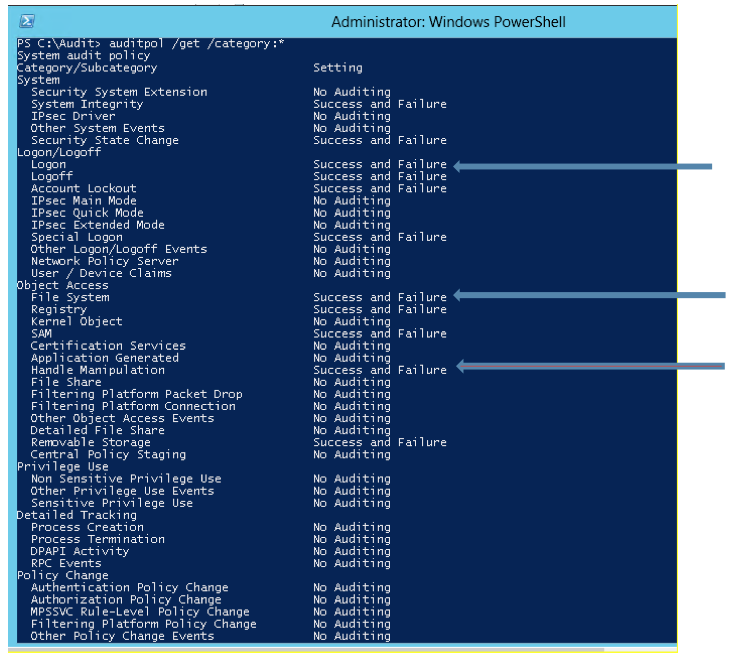
Check the system audit policy setting
- On the Windows server open a PowerShell window (Please make sure to launch this window with Administrative credentials).
- Run the command Auditpol /get /category:* to get the following screen
- If any of the highlighted audit entries are not enabled, please contact your Network Administrator and get a GPO policy configured for the OU that contains this server object. Guidelines for setting Advanced Audit Polices for LT Auditor+ are available at https://bluelance.com/wp-content/uploads/2015/03/LT-Auditor-Advanced-Auditing-Policies-Settings-.compressed.pdf
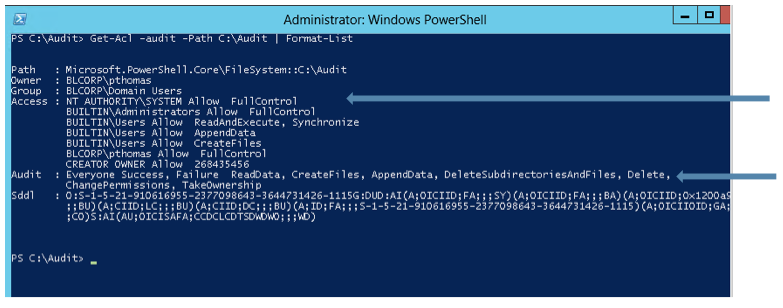
Check ACL entries for the folder to be audited
- From the PowerShell window run the command Get-Acl –audit –Path
| Format-List where- Analyze the entries for Audit and confirm that the Principals, Success/Failure settings and operations to audit are configured to collect the required data. If this is not enabled using Windows Explorer right click on the folder, click properties, highlight the security tab, click on Advanced and finally click on the Auditing tab to define the auditing entries for this folder and sub folders. Please select desired operations to audit from the list provided.
- If the LT Auditor+ service is using the System account, this account should have Allow FullControl rights on the server. If the service account is not being used, please ensure that the user account used by the service has Allow FullControl on the local server
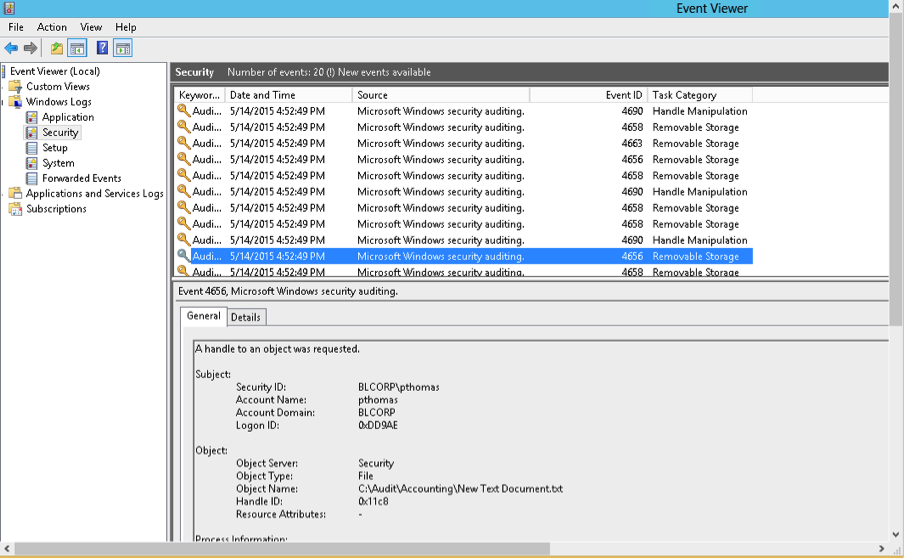
Confirm that audit policies are configured correctly
- Perform some activity on the folder to be audited such as creating, modifying or deleting a file. For example create a new text document.
- Open the event viewer and access the security logs. If the event 4656 shows up as shown below, this will confirm that Windows audit policies have been successfully configured to audit this folder.
Checking LT Auditor+ File Filter Policies
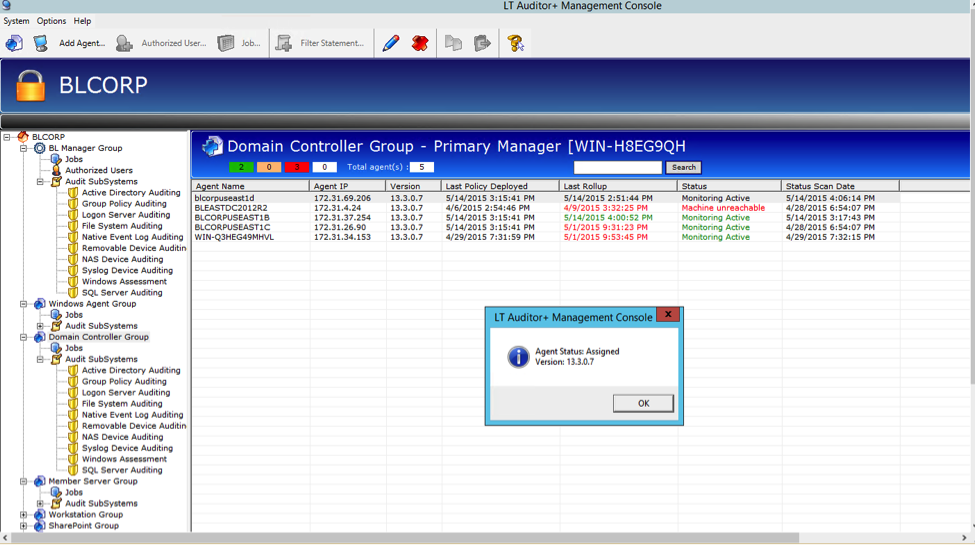
Ensure that Windows Agent machine is assigned
- Open the LT Auditor+ Manager and access the group that contains the Windows Server.
- Highlight the Windows server in question and double click the machine to get back the message stating the agent machine is assigned as shown below:
- If you see the message ‘It is not possible to connect’ this indicates that either the LT Auditor+ service is not running on the agent server or a firewall has blocked port 2877 for TCP/IP traffic required by LT Auditor+. In either of these cases no filter policy will get deployed and this issue will have to get resolved.
- If you see the message ‘Agent Status: Free Agent’ this indicates that the agent machine is not assigned to the LT Auditor+ Manager. This can happen if the agent machine was reimaged without being detached from the LT Auditor+ Manager. To resolve, please upgrade to HF1307. With HF1307 LT Auditor+ will automatically reassign a free agent with the double click operation performed in step 2 above.
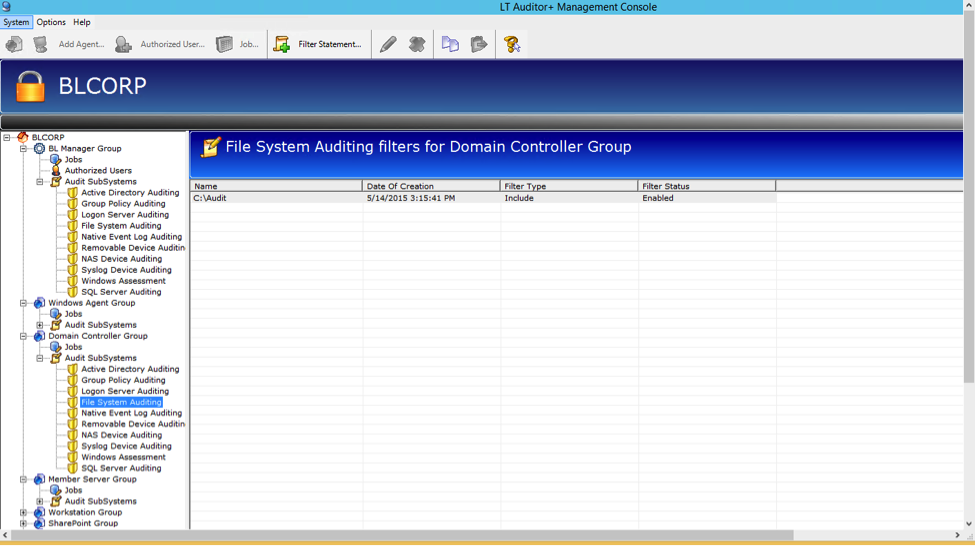
Check if the there is a file filter policy
- Highlight File System Auditing and confirm that a filter policy exists to audit file activity.
- If this is not set please refer to https://bluelance.com/wp-content/uploads/2015/03/LT-Auditor-Configuration-Guide-2013.compressed.pdf for documentation to configure LT Auditor+ policies.