Microsoft Windows operating systems uses a variety of authentication technologies that allow users access to resources on the network. These authentication protocols include Kerberos, NT LAN Manager (NTLM), Negotiate, Schannel (secure channel) and Digest which are all part of the Windows security architecture.
LT Auditor+ 2013 is able to completely audit all activity associated with Kerberos and NTLM authentication.
Kerberos
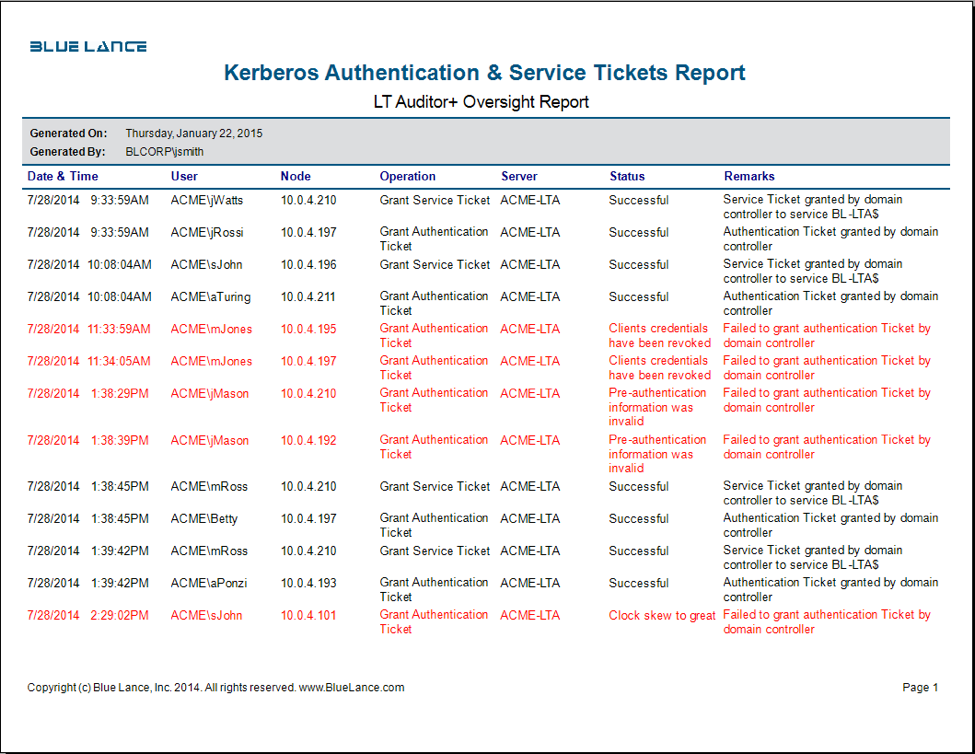
The Kerberos authentication protocol is the default authentication protocol for Active Directory (AD) authentication. Kerberos comprises the Key Distribution Center (KDC), the client user, and the server. The KDC is installed on a Windows AD Domain Controller and authenticates a user using the Authentication Service (AS) and the Ticket-Granting Service (TGS). All access by users to resources on the network will require a valid security token or ticket granted by the KDC. The following report is a record of Kerberos authentication activity recorded in LT Auditor+ 2013.
NTLM
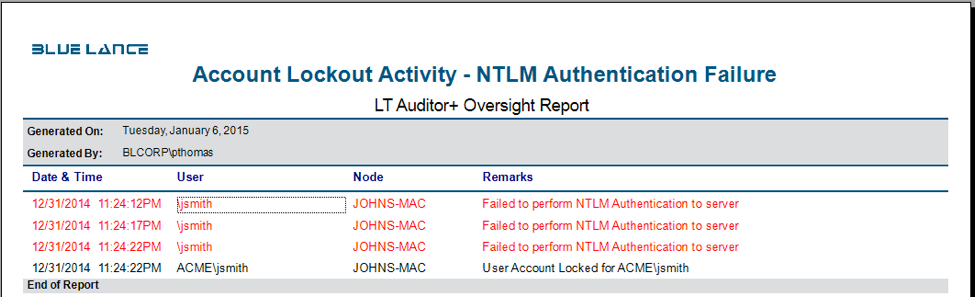
NTLM protocol uses a challenge-response methodology in which the client sends the username to a Windows server. The server generates and sends a challenge to the client which the client encrypts using the user’s password. This encrypted message is sent back as a response to the server. For local user accounts, the server validates the user’s response by looking into the Security Account Manager (SAM). For domain accounts, the server forwards the response to a domain controller for validating based on the group policy configured for user accounts. The following report is a record of NTLM authentication activity recorded in LT Auditor+ 2013.
Windows permits several types of logons used for different purposes, and LT Auditor+ 2013 can track and monitor every type of Windows logon activity as described below.
Interactive Logon
An interactive logon occurs for the following scenarios:
- User logons directly at the console.
- Logons remotely, through Terminal Services.
There are different types of Interactive logons:
- Local Logon. Local logon happens when the user logs in to the local SAM system. With local logon, the user will only have access resource on the local machine.
- Domain Logon. In this scenario, the user provides domain credentials to log on to the domain. Windows will use one of the protocols discussed above to authenticate to the domain.
- Smart Card Logon. Here the user inserts a smart card into a reader for authentication to the domain or local machine, allowing for multi-factor authentication.
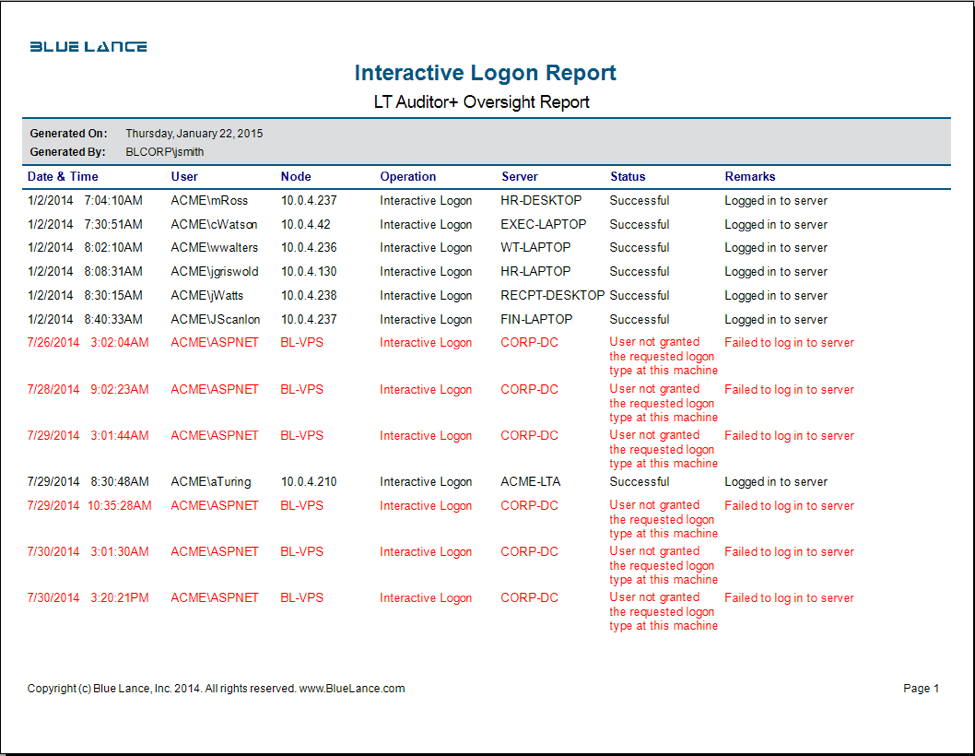
LT Auditor+ can audit and track all interactive logon activity as shown in the report below:
Network Logon
After a user is authenticated to the network, access to shared folders, printers, and other resources will generate a network logon. This information is useful to track to which servers a user connected after authenticating to a domain. Network logon activity occurs all the time, and this type of activity creates voluminous logs.
Batch Logon
Credentials used for scheduled tasks in Windows generates a Batch logon event.
Service Logon
Credentials used for services in Windows generates a Service logon event.
Unlock logon
This event occurs when a user returns to the console and unlocks a password-protected screen. This is a useful event to track on workstations.
New Credentials
Credentials used with the ‘Run As’ command to start a program will generate this event.
Cached Interactive
Windows caches the hashes of the last 10 interactive domains by default. When the client is not connected to the network or when no domain controller is available, Windows will use these hashes to verify the identity of the logon with a domain account creating a cached logon event.
Remote Interactive
When using the Windows RDP utility to connect to a machine, a remote interactive logon event is generated.
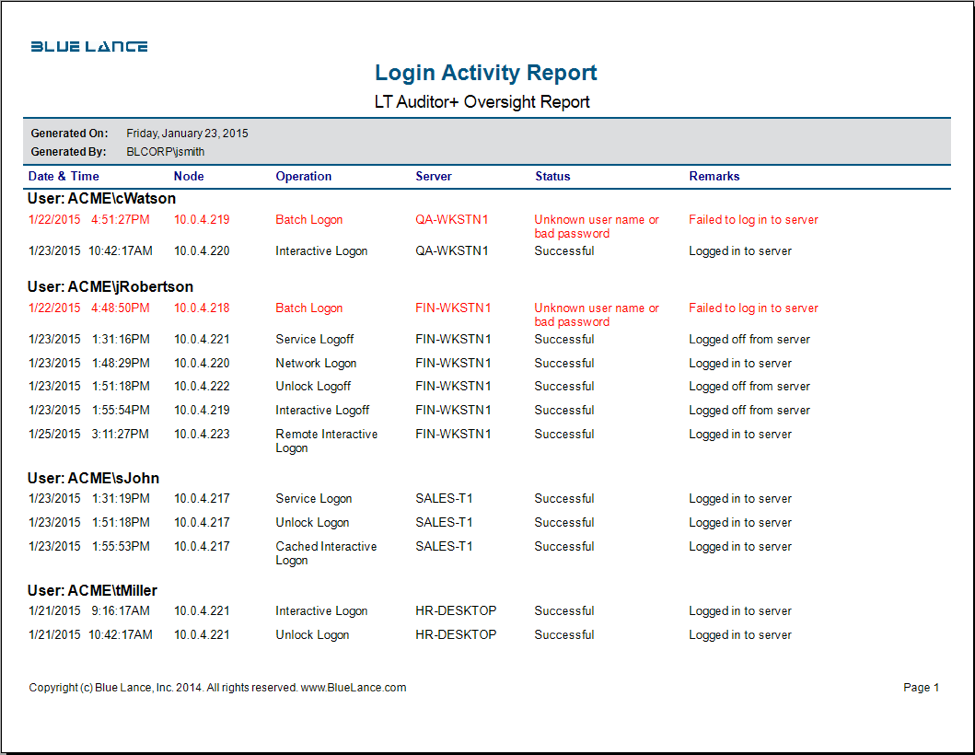
LT Auditor+ 2013 can capture all these events as shown in the attached reports.
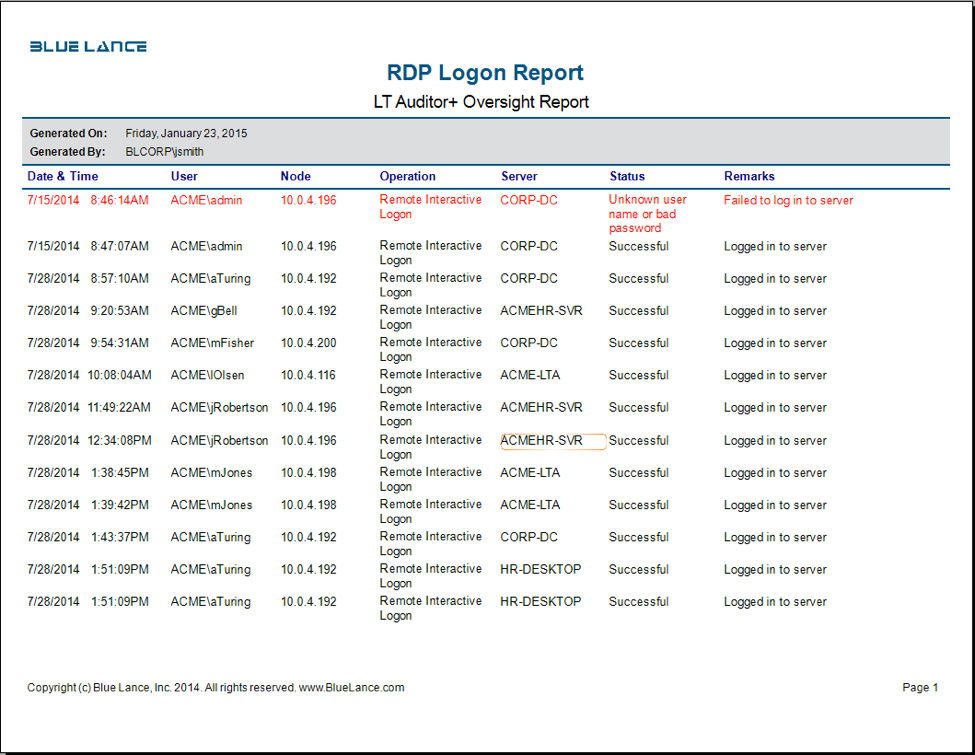
Users have the capability to use granular filters to collect and report on any of these type of logons.
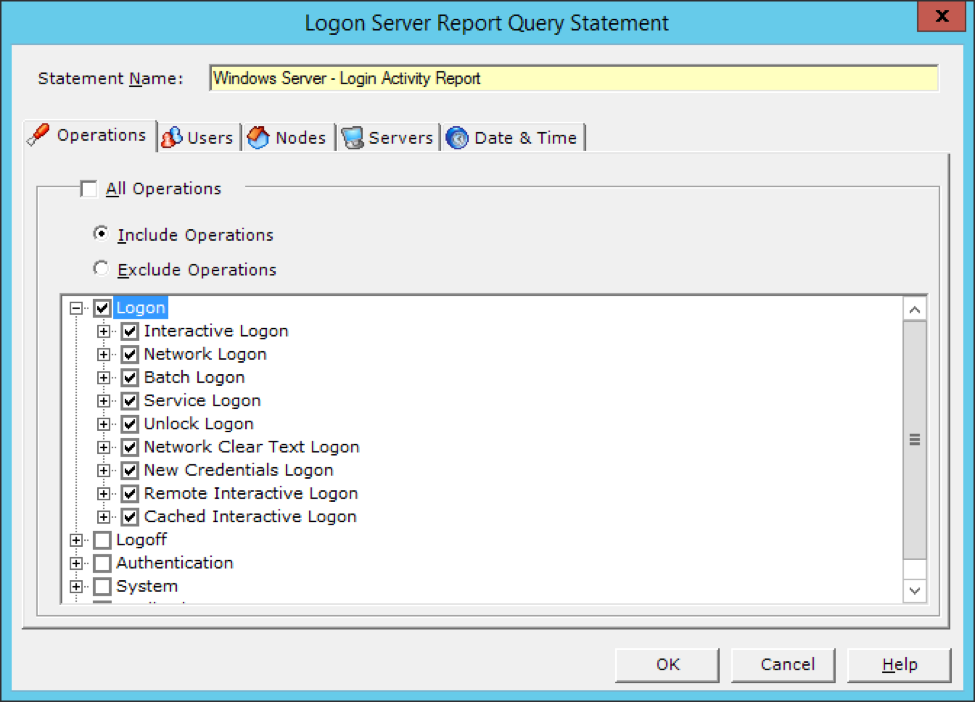
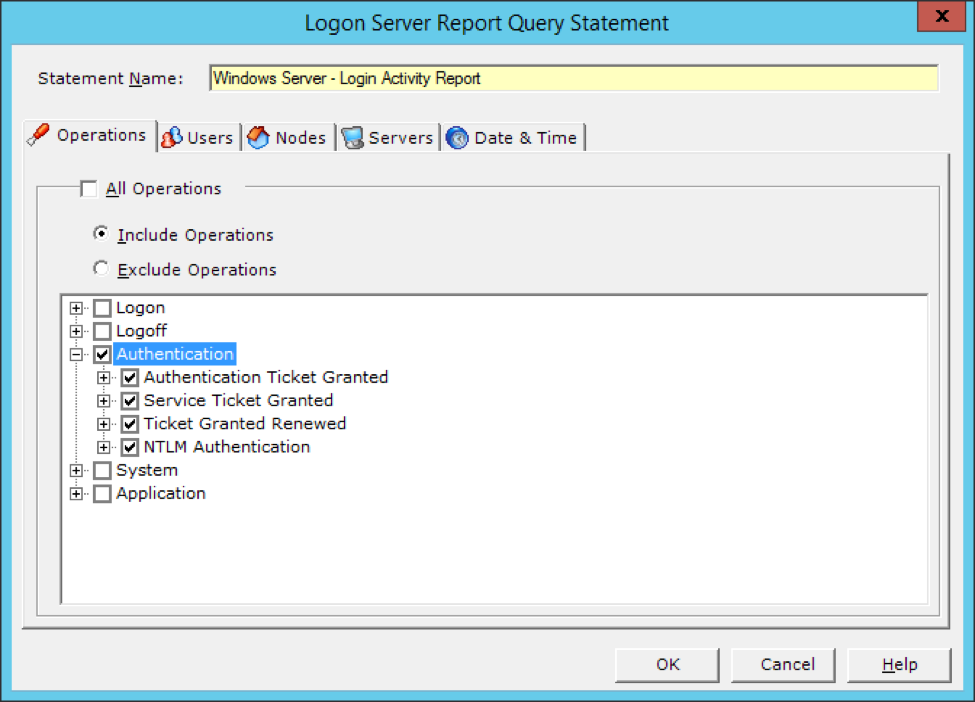
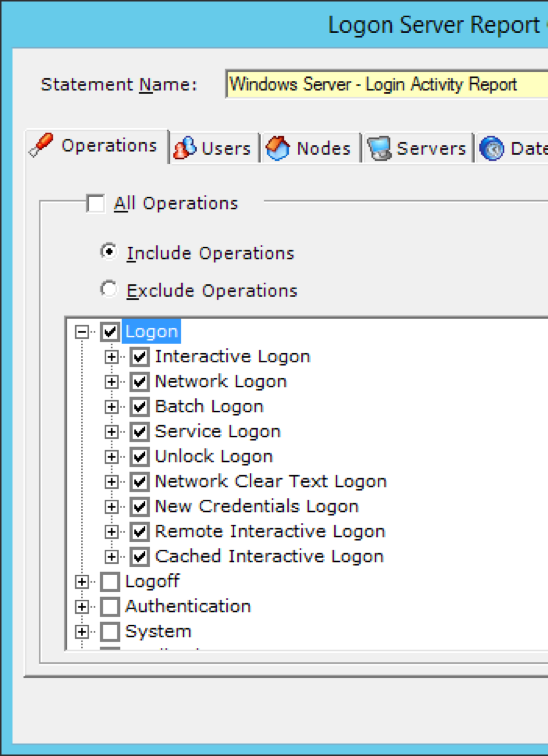
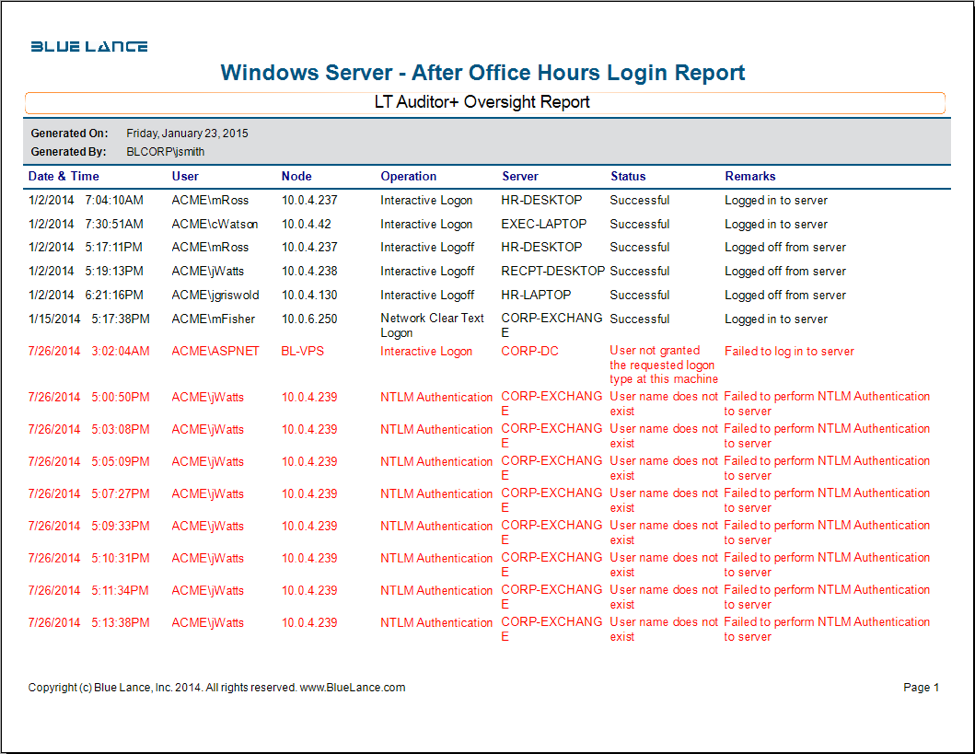
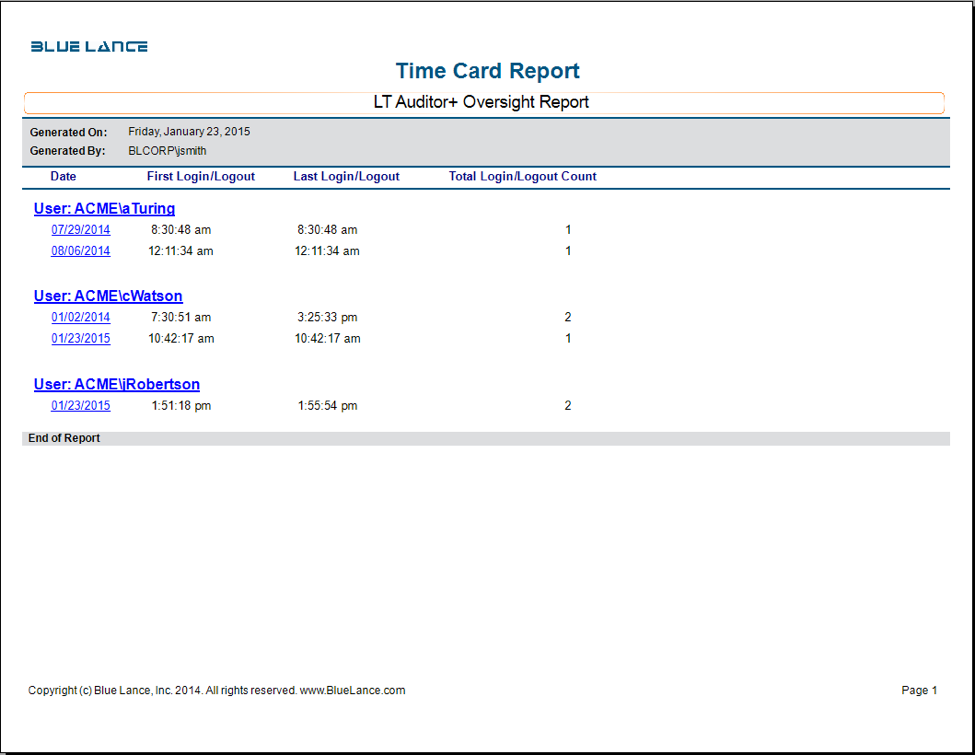
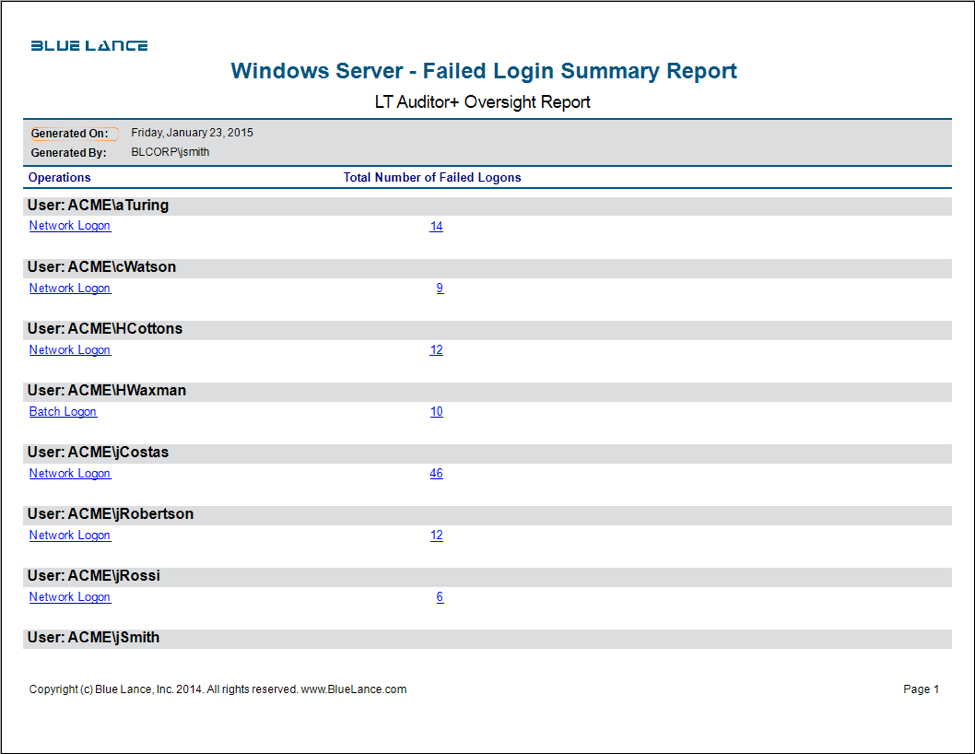
Investigative LT Auditor+ Logon Report Templates
- After Hour Logon Report
- Time Card Report
- Failed Logon Summary Report
- Failed Logon Detailed Report
About LT Auditor+
LT Auditor+ is a suite of applications that provide real-time monitoring and auditing of Windows Active Directory and Windows Servers changes. The application audits-tracks-reports on Windows Active Directory, Windows Workstations Logon/Logoff, Windows File Servers, and Member Servers to help meet security, audit, and compliance demands or requirements. Track authorized/unauthorized access of users’ Logon/Logoff, GPO, Groups, Computer, OU, and DNS server changes with over 300 detailed event-specific reports and real-time email alerts. Reports generation can be automated, scheduled, and exported to multiple formats like PDF, Excel, HTML, and CSV that further assist with a forensic investigation.







Leave A Comment