Group Policy is a core component of Active Directory (AD) used to centrally manage an organizations’ security, application, and user settings. Group Policy settings are divided into user and computer sections, and a policy can be configured to be applied based on whether the target is a user or computer object.
An extensive range of functionality is covered with Group Policies, such as:
- Password and account policy
- OS (Operating System) auditing
- Network and security options
- Public key encryption
- Registry settings
- Defining software distribution and restricting which software can run
- Internet Protocol Security (IPSec) policies
- Restricting group membership, file, registry, and service Access Control Lists (ACLs)
- User rights for operations, Start Menu, Control Panel, and Desktop configuration
All Group Policy Objects (GPOs) contain Administrative Templates that can be used to modify the registry on target machines. The HKEY_LOCAL_MACHINE and HKEY_CURRENT_USER are registry hives influenced by the Computer and User GPOs respectively.
LT Auditor+ 2013 can monitor all changes to GPO setting and provide a record of before-and-after changes clearly identifying who made these changes.
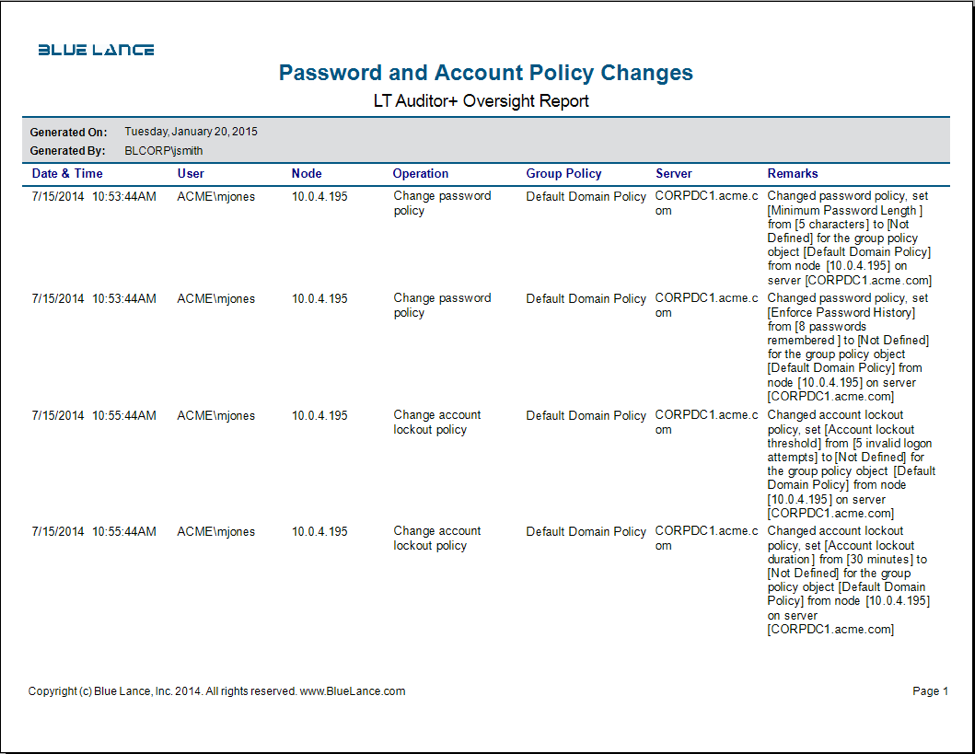
GPOs are applied to users or computers using one or more of the following methods:
- Linking to an AD container (domain, site, OU). The GPO will apply to any user or computer objects within the container and sub-containers.
- Security Filtering. Here Discretionary Access Control Lists (DACLs) on a GPO will determine which user/group or computer accounts will receive this GPO.
- Windows Management Instrumentation (WMI) Filtering leverages WMI to target computers to receive this GPO.
LT Auditor+ can capture exactly how a GPO was applied by auditing GPO links created or deleted and by monitoring changes to security filtering, WMI filtering, and Delegation changes.
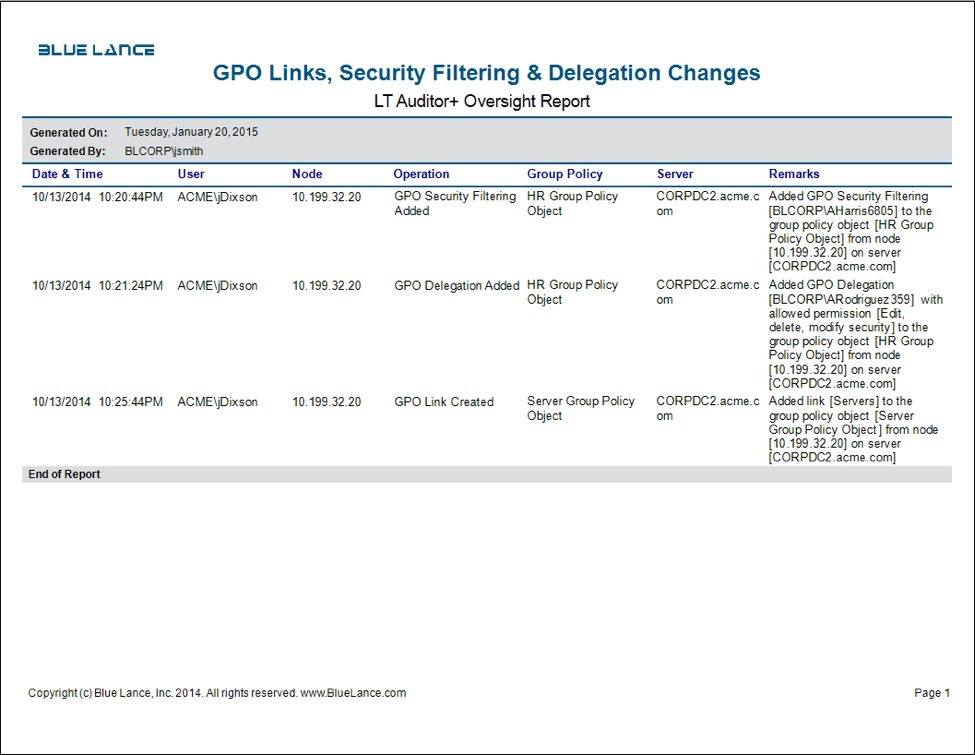
As there are multiple GPOs that can be used, it is important to understand how Windows determines the effective GPO applied for computers and users. The effective GPO is computed as follows:
- If any local GPO policies exist on a member server, this is applied first.
- Next, at the site level, if any GPO policies exist, they are applied.
- Next, domain level policies are applied.
- Lastly, policies at the OU level are applied, starting from the topmost OU down to child OU, where the computer or user is stored.
GPO policies are cumulative as long as there is no conflict. If there is a conflict, the last GPO applied becomes effective.
There are no specific GPO auditing features built into Windows, which is why it critical to use an application like LT Auditor+ to monitor and track changes. Here are some of the core weaknesses identified in the GPO architecture, which provides the added business justification to use LT Auditor+ 2013:
- Confidentiality. Since all users must have read access to a GPO, coupled with the fact that GPOs are not encrypted, an attacker can use GPO settings as reconnaissance for secondary attacks across the network.
- Availability. A wrongly configured GPO can cripple a network if applied to all machines and users on the network. This is why real-time notification of changes to domain policies or domain controller polices should be tracked so as to quickly mitigate mistaken or malicious actions on GPOs.
- Integrity. As GPOs reside on the DC file system in SYSVOL folder, an attacker with access to this volume can technically make changes to a GPO directly without using GPMC. This can impact the integrity of the GPO and can severely impact an organization. Using LT Auditor+ to monitor access to the GPO files can protect the Active Directory environment.
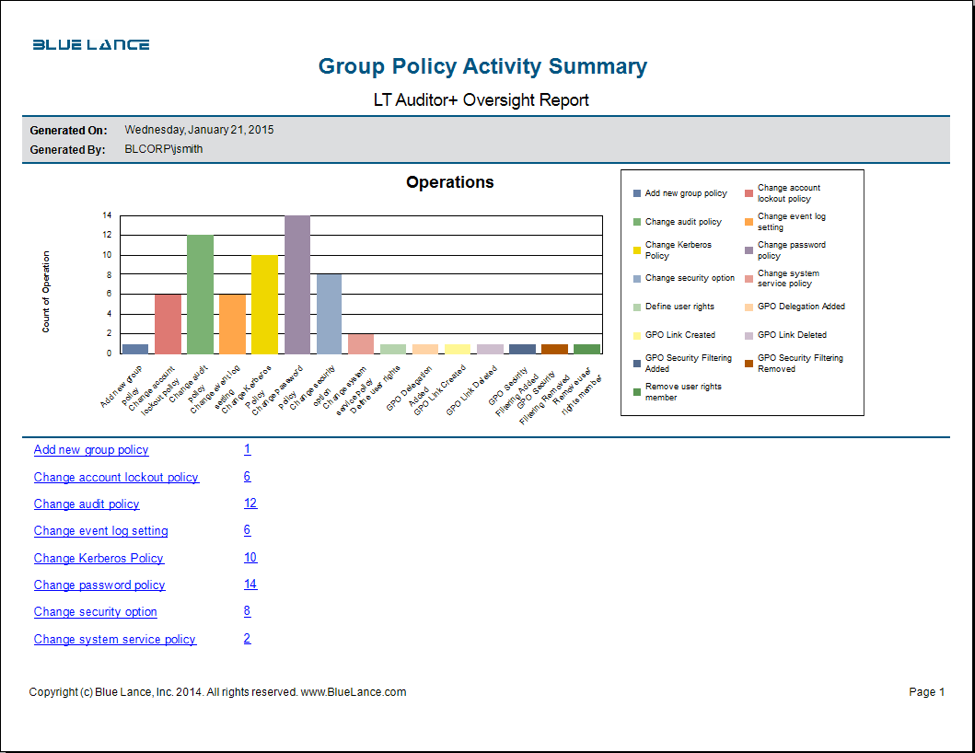
Potential GPO Vulnerabilities and Attack Points
As GPO setting files are not encrypted, they can be dumped and analyzed for follow on attacks. The two default policies (Domain and Domain Controller) have well-known GUIDs and are an easy starting point. Reading the attributes gpLink and gpOptions settings for the domain and the Domain Controllers, OU can help attackers identify exactly which GPOs are being applied to the domain and domain controllers.
A few important settings that should be monitored for attacks are:
- Password/Account Settings. The minimum password length can be used to optimize password cracking programs. The account lockout policy can be used for DOS attacks.
- Services Running. Identifying services that are enabled allows attackers to target network points without raising their profile.
- Restricted Groups. This provides information on privileged groups that can be used to target password cracking on privileged accounts.
- Security Options. Improper configuration can cause the machine to be exploited for attacks. Turning on the ‘Guest’ account is an example of significantly increased risk.
- IPSec Policies — If IPSec is being used for packet/port filtering, then this knowledge of firewall/router rules can be leveraged to target attacks.
About LT Auditor+
LT Auditor+ is a suite of applications that provide real-time monitoring and auditing of Windows Active Directory and Windows Servers changes. The application audits-tracks-reports on Windows Active Directory, Windows Workstations Logon/Logoff, Windows File Servers, and Member Servers to help meet security, audit, and compliance demands or requirements. Track authorized/unauthorized access of users’ Logon/Logoff, GPO, Groups, Computer, OU, and DNS server changes with over 300 detailed event-specific reports and real-time email alerts. Reports generation can be automated, scheduled, and exported to multiple formats like PDF, Excel, HTML, and CSV that further assist with a forensic investigation.







Leave A Comment