Access to files and folders is controlled by permissions or Discretionary Access Control Lists (DACLs) assigned to folders and files. In an Active Directory (AD) environment, user access to file and folder resources is governed by DACLs assigned directly or based on memberships to groups that have been granted permissions to these resources.
LT Auditor+ 2013 can scan and provide detailed reports on permissions granted to principals or trustees on sensitive or critical files and folders. LT Auditor+ 2013 can also provide real-time notification to changes to these permissions.
Windows categorizes permission as:
- Basic or standard permissions
- Special or advanced permissions
The following table from Microsoft details basic permissions allowed on Windows New Technology File Systems (NTFS):
| Permission | Meaning for Folders | Meaning for Files |
|---|---|---|
| Read | Permits viewing and listing of files and subfolders | Permits viewing or accessing of the file’s contents |
| Write | Permits adding of files and subfolders | Permits writing to a file |
| Read & Execute | Permits viewing and listing of files and subfolders as well as executing of files; inherited by files and folders | Permits viewing and accessing of the file’s contents as well as executing the file |
| List Folder Contents | Permits viewing and listing of files and subfolders as well as executing of files; inherited by folders only | N/A |
| Modify | Permits reading and writing of files and subfolders; allows deletion of the folder | Permits reading and writing of the file; allows deletion of the file |
| Full Control | Permits reading, writing, changing, and deleting of files and subfolders | Permits reading, writing, changing, and deleting of the file |
Advanced or special permissions are logical groupings of the combination of basic permissions. This table from Microsoft defines these permissions:
| Permission | Description |
|---|---|
| Traverse Folder/Execute File | For folders: Traverse Folder allows or denies moving through folders to reach other files or folders, even if the user has no permissions for the traversed folders (applies to folders only). Traverse folder takes effect only when the group or user is not granted the Bypass traverse checking user rights in the Group Policy snap-in. (By default, the Everyone group is given the Bypass traverse checking user rights.) For files: Execute File allows or denies running program files (applies to files only). Setting the Traverse Folder permission on a folder does not automatically set the Execute File permission on all files within that folder. |
| List Folder/Read Data | List Folder allows or denies viewing file names and subfolder names within the folder. List Folder only affects the contents of that folder and does not affect whether the folder on which you are setting the permission will be listed. Applies to folders only. Read Data allows or denies viewing data in files (applies to files only). |
| Read Attributes | Allows or denies viewing the attributes of a file or folder, such as read-only and hidden. Attributes are defined by NTFS. |
| Read Extended Attributes | Allows or denies viewing the extended attributes of a file or folder. Extended attributes are defined by programs and may vary by program. |
| Create Files/Write Data | Create Files allows or denies creating files within the folder (applies to folders only). Write Data allows or denies making changes to the file and overwriting existing content (applies to files only). |
| Create Folders/Append Data | Create Folders allows or denies creating folders within the folder (applies to folders only). Append Data allows or denies making changes to the end of the file but not changing, deleting, or overwriting existing data (applies to files only). |
| Write Attributes | Allows or denies changing the attributes of a file or folder, such as read-only or hidden. Attributes are defined by NTFS. The Write Attributes permission does not imply creating or deleting files or folders, it only includes the permission to make changes to the attributes of a file or folder. In order to allow (or deny), create, or delete operations, see Create Files/Write Data, Create Folders/Append Data, Delete Subfolders and Files, and Delete. |
| Write Extended Attributes | Allows or denies changing the extended attributes of a file or folder. Extended attributes are defined by programs and may vary by program. The Write Extended Attributes permission does not imply creating or deleting files or folders, it only includes the permission to make changes to the attributes of a file or folder. In order to allow (or deny), create or delete operations, see Create Files/Write Data, Create Folders/Append Data, Delete Subfolders and Files, and Delete. |
| Delete Subfolders and Files | Allows or denies deleting subfolders and files, even if the Delete permission has not been granted on the subfolder or file (applies to folders). |
| Delete | Allows or denies deleting the file or folder. If you do not have Delete permission on a file or folder, you can still delete it if you have been granted Delete Subfolders and Files on the parent folder. |
| Read Permissions | Allows or denies reading permissions of the file or folder, such as Full Control, Read, and Write. |
| Change Permissions | Allows or denies changing permissions of the file or folder, such as Full Control, Read, and Write. |
| Take Ownership | Allows or denies taking ownership of the file or folder. The owner of a file or folder can always change permissions on it, regardless of any existing permissions that protect the file or folder. |
LT Auditor+ 2013 can scan files and security permissions (DACLs) assigned or inherited. This information is valuable to ensure that security administrators document and validate who should and should not have permissions to resources in the directory. The following report shows permissions that were scanned for a folder with LT Auditor+ 2013.
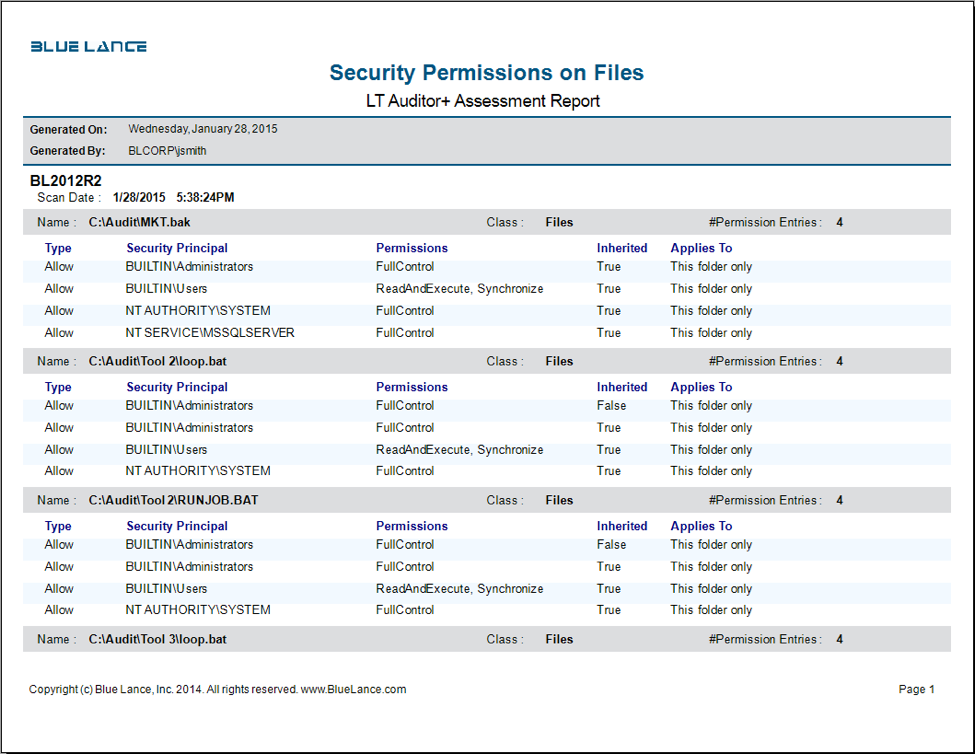

Changes to these permissions are also monitored with LT Auditor+ 2013.

Benefits of scanning and monitoring for File/Folder permissions with LT Auditor+
- Comply with principals of least privilege and ‘need to know’ by identifying sensitive Files and Folders with excessive rights for remediation.
- Enable security administrators to quickly check for authorization and validation with real-time notification of when permissions on important Files are changed.
- Meet compliance requirements from SOX, PCI-DSS, HIPAA, FFIEC, and NIST by demonstrating vigilance in scanning for such activity.

About LT Auditor+
LT Auditor+ is a suite of applications that provide real-time monitoring and auditing of Windows Active Directory and Windows Servers changes. The application audits-tracks-reports on Windows Active Directory, Windows Workstations Logon/Logoff, Windows File Servers, and Member Servers to help meet security, audit, and compliance demands or requirements. Track authorized/unauthorized access of users’ Logon/Logoff, GPO, Groups, Computer, OU, and DNS server changes with over 300 detailed event-specific reports and real-time email alerts. Reports generation can be automated, scheduled, and exported to multiple formats like PDF, Excel, HTML, and CSV that further assist with a forensic investigation.
